Did you know that on average, every company is connected to ten third-party businesses?
There’s the payroll services company that remotely manages employee wages. The Software-as-a-Service (SaaS) cloud storage provider that backs up customer account data. The security company that provides access control to company buildings and systems.
To achieve an efficient supply chain, organizations rely on each other. When all parts of the chain are working well together, the result can be a streamlined and successful process, benefiting all involved.
But there’s a flipside. When companies are connected, the risk of one is the risk of all, and any disruptions can quickly spread throughout the entire chain.
If one company suffers a breach, it can quickly spread to impact the data it works with and disrupt the entire supply chain. That’s why third-party risk management (TPRM) is crucial to prevent and mitigate these types of impacts.
What Is Third Party Risk Management?
Most organizations have an average of ten third party relationships, but some maintain over 100 third-party connections. Whatever the number, organizations need a uniform method of assessing and addressing third party risk.
Third Party Risk Management establishes this uniform process. It’s the practice of evaluating and reducing business risks that originate with or are associated with, third-party partners.
The TPRM process begins before an organization enters into a contractual business relationship with a third party and continues throughout the lifecycle of that partnership.
Why Is Third Party Risk Management Important?
In the digital age, everything is about data, regardless of business sector.
Health providers offer care but oversee sensitive health data. Manufacturers build, but they also generate technical specs, blueprints and other intellectual property.
Many finance companies are all digital—nothing more than payment, investment, and transaction data. Retail companies hold onto customer data to serve them better.
Third parties have access to all this data, information, and property that primary organizations rely on to function and succeed. It might include customer details and credit card numbers, financial information, intellectual property (IP) and trade secrets, private health information, and employee data, such as Social Insurance Numbers (SINs), addresses, passwords, login credentials, and more.
Organizations cannot risk any loss, theft, or compromise of this data. In some cases, like IP and trade secrets, business success hinges on information secrecy and safekeeping.
The same is true for businesses that collect personally identifiable customer data. They are often legally responsible for this data for the duration of its lifecycle, including time spent in third party hands.
TPRM is a critical part of modern-day business. It helps organizations identify and mitigate potential risks from vendor relationships.
By avoiding compromising situations, organizations lessen the chance that they will encounter financial, reputational, and regulatory fallout from problems originating with third party vendors, contractors, and suppliers.
Third Party Risk Management Lifecycle
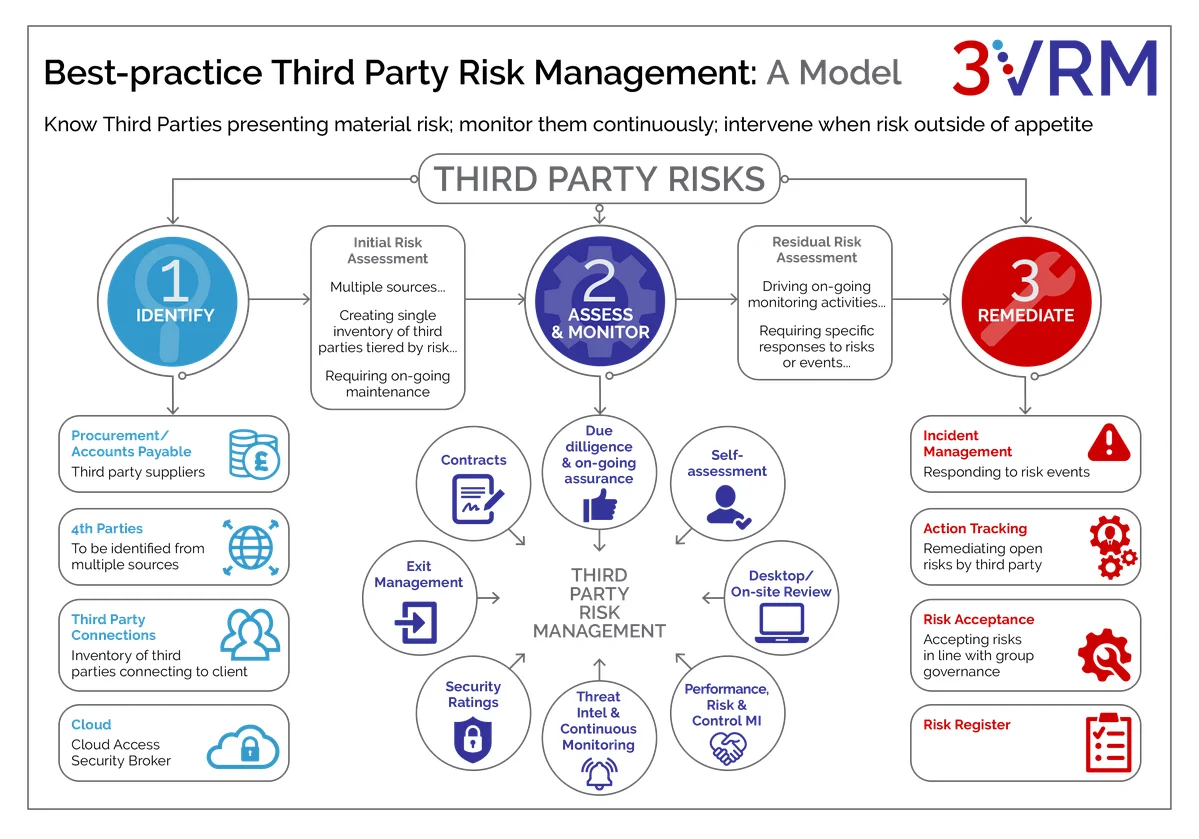
Source: 3VRM
A helpful way to approach the relationship with third parties is through a “lifecycle” lens. Think of a relationship with every third-party vendor as you would a marriage or a friendship.
An organization finds a suitable vendor in a pool of candidates, the relationship begins, evolves and sometimes ends. TPRM entails different processes depending on the stage of the relationship. Here are the key stages.
Identification: Decide whether you need a third-party vendor to handle this part of your business operations. Do the cost savings justify the potential risk? If so, gather a list of potential candidates.
Due Diligence: Investigate the candidates, their jurisdictions, projects, and activities to highlight any potential risks. Find out if they are the right vendor to do the job. Do they have the time, the resources, and the expertise? Do they share your business values? What security certificates do they have?
Shortlisting: Based on the due diligence performed, produce a shortlist of most desirable third-party candidates. Be transparent about risks identified in the remaining shortlisted candidates.
Questionnaire: Send a risk questionnaire to shortlisted candidates that asks about ownership and location, financial health, credit history, compliance practices, Information Technology (IT) practices and policy. Ask about past involvement in any compliance or data breaches.
Contracting: After completing the necessary groundwork, select a suitable third-party vendor. Be clear about security expectations during contract negotiation and make your security requirements explicit in the terms and conditions of the contract.
Onboarding: Get the third party up to speed with your processes, policies, and protocols. Provide cyber security training to third-party employees to ensure they follow security best practices when dealing with your company data.
Ongoing Monitoring: After onboarding is complete, the business relationship continues to evolve. Organizations need to perform continuous monitoring to review compliance and ensure controls remain in place. Perform regular audits to ensure third parties are meeting Service Level Agreements (SLAs), key performance indicators (KPIs) and key risk indicators (KRIs). Keep detailed audit and compliance records.
Offboarding: When a relationship with a third party ends, there is still work to be done. Follow strict measures to revoke access to third party personnel and systems and return all data to the primary organization. Document the process for audit and compliance purposes.
Related reading: The Security Risks of Improper Employee Offboarding and How to Prevent It
Adopting a lifecycle lens reminds organizations that TPRM is not a one-time thing. Every time a new vendor is identified, the TPRM teams need to repeat the process.
Any of the above intermediate steps should also be revisited if there are substantial changes in third party ownership, in the economy, in legislation, in supply chains, or in geopolitical circumstances.
A political regime change with an overseas vendor, for example, could put IP at risk, or lead to new kinds of cyber threats.
Considerations When Onboarding Vendors
A strong TPRM process needs to begin even before an organization signs a contract with a new vendor. The negotiation period is a great time to discuss requirements and set expectations about security behaviours and practices down the road.
Those expectations can then be put in writing and form part of the contractual relationship. Here are the key details to consider during the onboarding process.
Do you have a repeatable onboarding process in place? Develop an effective onboarding process that’s repeatable for every new third-party vendor. When it’s part of company procedure, it’s easy to train new employees on the onboarding process and establish checklists and accountability.
Who has access? Third-party personnel need to access to your data and systems. It’s as if they’re working for you at a distance. Find out who that is on the vendor side and document their role and responsibilities.
If the third party changes personnel, stipulate that they notify you immediately. Have a procedure to withdraw access if the partnership ends or if accountable employees leave the company.
Related reading: What is a Zero Trust Network?
What is the risk level? Third parties pose different risk levels to your organization. A vendor located in your jurisdiction will likely face the same legal outcome in the case of data breach.
A remote vendor in a foreign country might face less scrutiny and pose a higher threat. Gauge these risk levels from day one and adjust security requirements and training accordingly.
Is the process simple and efficient? If TPRM onboarding is too complex or overly stringent, your TPRM team may use workarounds that can degrade the intent of the TPRM program.
If onboarding is slow or unwieldy, you may lose a competent or short-term vendor that can’t afford the time, or lose revenue yourself from work delays. Balance security needs with efficiency.
What Types of Risks Do Third Parties Introduce?
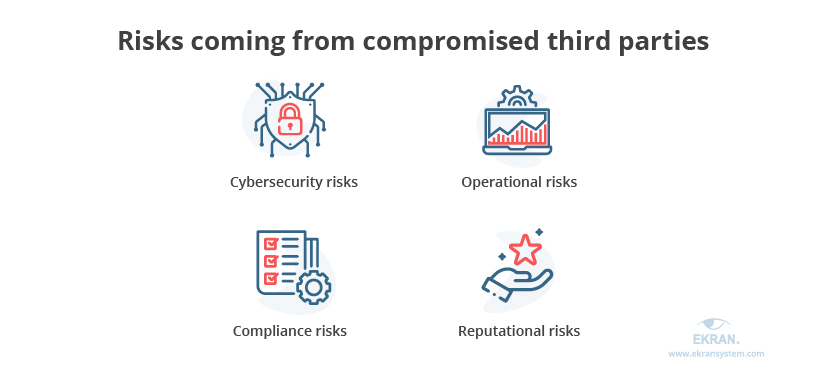
Source: Ekran System
Since data is the primary currency of the digital age, many third-party risks revolve around data loss, theft, or damage. These data compromises often generate associated risks. The following are the main risk areas to consider when assessing third-party relationships and implementing a TPRM program.
Cyber security: Third parties are a favorite attack vector for malicious actors since cyber security can be weaker at these organizations. Cyber attackers also often exploit vulnerabilities at smaller vendors and suppliers to launch attacks on larger and more valuable clients upstream.
It is crucial to implement cyber security awareness training to ensure all business units follow cyber security best practices.
Regulatory: Organizations are accountable for the data that enters their systems. When breaches lead to data privacy violations, primary business can face regulatory implications, even if the data is in third party hands.
Those risks extend to other kinds of legislation. If third parties are not compliant with labour or environmental law, for example, their partners risk liabilities and penalties.
Financial: Security breaches can significantly harm the financial posture of an organization. Data loss can cause reputational harm and lead to loss of customers and future revenue.
A security breach could force an operational pause or stoppage, severely impacting cash flow. Data breach remediation can be expensive, as can ransom payments that cyber attackers demand in ransomware attacks.
Related reading: What’s the Damage? The Truth About the Cost of Data Breaches
Operational: Third party activity could force a shutdown at the primary organization, but other issues can also lead to business disruptions at partner organizations, such as network downtime, technology or equipment problems, employment shortages or disputes, or weather events.
Reputational: Legislation and industry standards increasingly require organizations to inform customers about data security incidents, even if third-party vendors caused them. When vendors perform irregular actions or provide sub-standard service, customers make no distinction.
Those negative experiences brush off on the primary organization, harming reputation and the customer relationship.
Strategic: Organizations need to be in strategic alignment with their partners. If downstream vendors make business decisions that compete with priorities, or the means and possibility of achieving them, that creates a strategic risk.
When assessing third-party risks, keep in mind that risks in a single area, such as cyber security, often give rise to reputational, financial, operational, and regulatory risks.
Why You Should Invest in Third Party Risk Management
Investing in TPRM can seem counterintuitive when the point of engaging a third-party vendor in the first place is to lower costs through outsourcing or automating non-core functions. When budgets are tight, business leaders may feel that TPRM is not worth the outlay of time, personnel, and money.
Given the significant risks that third-party partnerships pose, however, the upfront investment in TPRM pays off in the long run. The cost of remediating a cyber security event, for instance, can be substantial, and the risk of these events is on the rise.
Severe data breaches hobble organizations while they stick-handle the legal ramifications and struggle to win back customers and restore their reputations.
The cost of these disruptions adds up quickly. During recovery, organizations risk losing ground and ceding market share to competitors. In the final calculation, the cost of prevention is the better deal.
What Does Third Party Risk Management Entail?
Effective TPRM programs can take many forms depending on the sector, type, number, and location of vendors engaged, and other factors.
Regardless of those differences, a robust TPRM program focuses first on the primary organization's most valuable assets and gains insights into the security maturity of the vendors that handle them. Lastly, it builds an action plan to secure those items. Here are the steps:
- Identify the organizational assets that require protection. Determine and rank their value.
- Define the risks and the potential threats to those assets. Identify the cyber attack surface, that is, the area(s) of an organization that are vulnerable to attack.
- Assess whether the third-party vendor has proper controls and safeguards in place to protect the assets in the most efficient and robust way possible.
What are the Common Challenges of Third Party Risk Management?
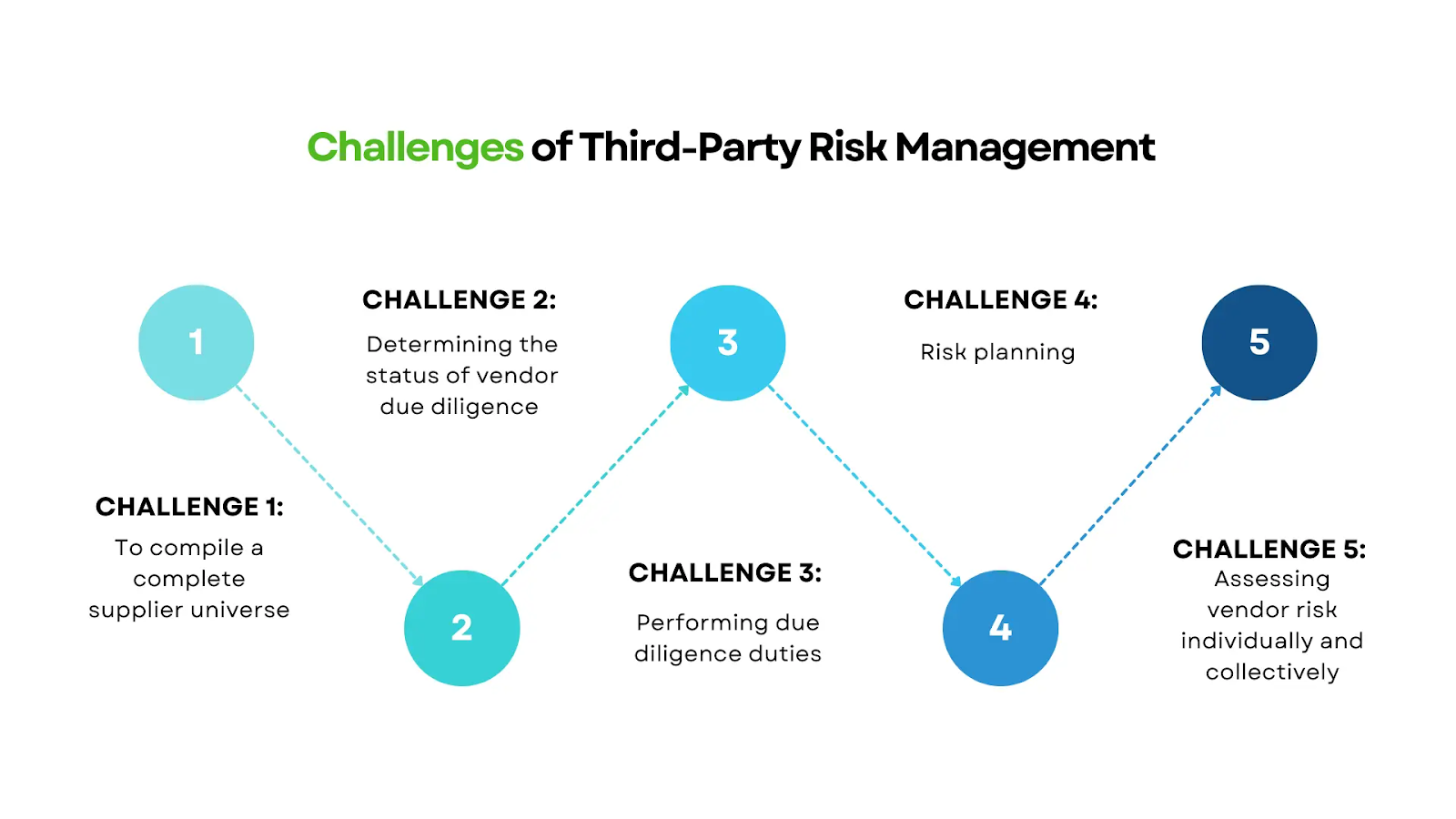
Source: SignalX
For organizations that haven’t yet implemented TPRM, the biggest challenge is instituting a program. Organizations that haven’t yet faced fallout from a third-party cyber security breach may not fully grasp the risks and continue to delay setting TPRM in motion.
The risk of cyber security attacks through third party vectors is rising, and that inertia can be damaging or even fatal to organizations.
Information gathering can present a major challenge, especially as vendor networks grow more complex. Organizations need to maintain detailed inventories of their third-party relationships, but they also need details about fourth parties in their vendors’ orbits.
Information acquired during due diligence needs constant updating and reconciling with newer data from relevant business units—not an easy job.
The nature of third-party relationships can leave communication gaps between organizations. To mitigate risks, TPRM teams need to communicate policy expectations clearly—not only at the beginning of the relationship, but at regular intervals.
Relevant business units should put procedures in place to reinforce transparent and structured communication channels.
The Vendor Risk Assessment Process
Vendor risk assessment takes a similar approach to the TPRM lifecycle, but focuses more directly on how the vendor handles consumer data originating with the primary organization.
Organizations need to assess the risk level of the vendor itself and the risk an organization faces by purchasing or using its technology or software.
In the case of data storage and processing solutions, risk assessment teams may need to seek the assistance of technology experts. Advice from an internal IT team or external consultant can provide insight into the working of those tools and assess their regulatory compliance.
On that basis, organizations can set a risk appetite in balance with the achievement of business goals.
Cyber Security Third Party Risk Management
To implement an effective and timely TPRM program for cyber security organizations need to identify program drivers, observe standard frameworks, and designate an internal team to carry out the program.
Organizations should look to industry standards on information security and privacy legislation in relevant jurisdictions and use those as guidelines to address and mitigate risk.
For example, Canadian commercial organizations that collect customer information must comply with Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA).
The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) issue joint frameworks that provide guidance on cyber security TPRM.
One common framework is ISO/IEC 27001:2022 – Annex A.15 – Supplier Relationships. This standard establishes a data-sharing agreement between organizations and suppliers to secure information along the supply chain.
This ISO certification forms part of an organization’s overall information security management system (ISMS).
ISO/IEC 27036-1:2021 – Cyber security — Supplier Relationships is another standard that organizations observe to protect information systems and the data that suppliers handle.
The standard provides a framework for organizations to implement a range of business management, risk management, operational, HR, and information security processes and controls.
Vendor Risk Management Best Practices
Given the heightened need for cyber security risk management, that’s where many organizations focus their energies. The following best practices help mitigate cyber security risks and reduce the likelihood of cyber attack indirectly through vendor technology and, especially, vendor employee actions.
Ensure your vendor has cyber security protections in place: Before signing a contract with a third party vendor, meet the IT department. Find out what access controls they have in place and what security testing and auditing procedures they perform.
Learn whether and how often employees undergo cyber security training, do phishing simulations, and social engineering testing.
Designate a team responsible for vendor risk management: Having team that focuses specifically on vendor relationships, monitoring, and auditing, helps mitigate cyber threats and other problems.
It can also help address incidents much more efficiently if they occur. Ensure senior management invests in the team by including them in the team membership.
Provide cyber security training: Make sure that vendor employees have the cyber security training you expect of your own employees. If specific personnel will access your data and systems, make sure they use secure file transfers, VPNs, and multi-factor authentication.
Provide training on credential protection, strong passwords, and can identify phishing emails and malicious links.
Monitor vendors continuously: Some organizations complete the onboarding process and assume that’s the end of the story. Cyber security risks can emerge at any point in the vendor lifecycle.
For example, new management or new employees might entail a policy change. One way of assessing vendor security is through security ratings, which function like credit scores.
Develop an incident response plan: Whatever organizations do to mitigate third-party risks, they still need a robust action plan in case something happens. Acting fast, with forethought, in the case of a third-party breach reduces downtime and expenses and can help contain reputational damage.
Assign clear duties to specific employees and incorporate incident management training beforehand.
Cyber Security Awareness Training is Essential in Third Party Risk Management
TPRM procedures are crucial to helping organizations gain insight into their cyber attack surface. Despite those efforts, human error is still the primary attack vector in the majority of cyber incidents—82% of them, according to a 2022 report by Verizon.
The best defense against security breaches is making sure that people with access to your data and systems follow cyber security best practices. Third party vendor employees need regular, high level cyber security training, testing, and performance assessment.
A great way to launch or re-evaluate a TPRM program is to run it past cyber security professionals. They can help improve an organization’s security posture and develop strategies to pinpoint and mitigate third party cyber security risk.
![]()
Cyber Security Hub: Access Exclusive Cyber Security Content
For more tips on building a cyber aware culture in your organization, visit our CyberHub.