Human Risk Management
Enhance your training program with fun, engaging security awareness content that supports cyber security leaders and their behavior change initiatives. Enjoy multilingual, mobile responsive, and accessible content that makes human risk management available to all users and promotes an inclusive atmosphere.
Quizzes
Test end user knowledge retention from your security awareness courses with quizzes that utilize different question formats. Pull from a bank of pre-configured quiz questions or create your own to ensure your users are receiving the most pertinent testing material and response feedback possible.
GENERAL KNOWLEDGE
End User
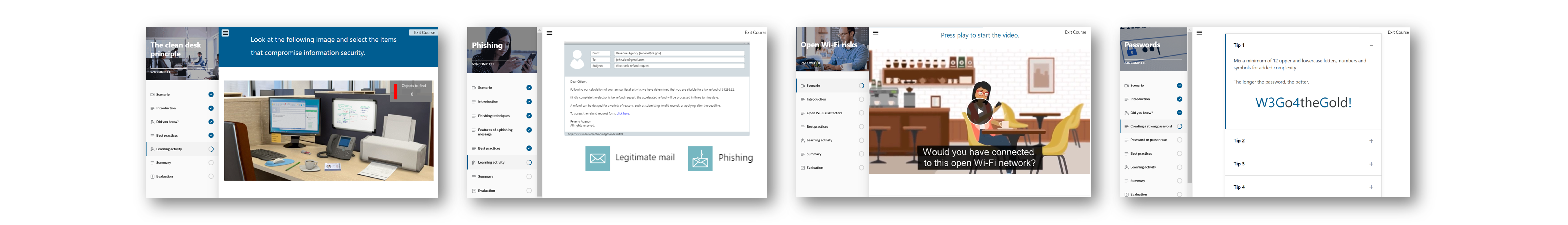
Designed to strengthen the human element of your organization’s information security, end user courses help participants understand best practices on a wide variety of cybersecurity topics. Each module includes interactive learning activities that reinforce those key messages.
- Access Control
- AI Risks and Best Practices
- Bring Your Own Device (BYOD)
- Business Email Compromise
- Cloud Services
- Confidentiality on the Web
- Data Leakage
- Identity Theft
- Incident Reporting
- Information Classification
- Information Lifecycle
- Intellectual Property
- Introduction to Information Security
- Malware
- Mobile Devices
- Open Wi-Fi Risks
- Password
- Phishing
- Phishing Websites
- Physical Security
- Privacy
- Protecting Payment Card Data
- Protecting Your Home Computer
- Ransomware
- Responsible Use of the Internet
- Smartphones
- Social Engineering
- Social Networks
- The Clean Desk Principle
- Traveling Securely
- Unintentional Insider Threat
- Working Remotely
Animated Trainings
Live Action Trainings

| Code | Topic | Description |
|---|---|---|
| 101 | Introduction to Information Security |
|
| 102 | Information Classification |
|
| 103 | Information Lifecycle |
|
| 104 | Intellectual Property |
|
| 105 | Passwords |
|
| 106 | Physical Security |
|
| 108 | Access Control |
|
| 201 |
| |
| 203 | Confidentiality on the Web |
|
| 205 | Social Engineering |
|
| 206 | The Clean Desk Principle |
|
| 207 | Privacy |
|
| 208 | Protecting Payment Card Data |
|
| 210 | Phishing |
|
| 211 | The Bring Your Own Device (BYOD) Trend |
|
| 301 | Malware |
|
| 304 | Responsible Use of the Internet at Work |
|
| 306 | Identity Theft |
|
| 307 | Social Networks |
|
| 308 | Working Remotely (Mobile Users) |
|
| 321 | Mobile Devices |
|
| 322 | Traveling Securely |
|
| 323 | Protecting Your Home Compute |
|
| 324 | Ransomware |
|
| 325 | Data Leakage |
|
| 326 | Business Email Compromise |
|
| 327 | Unintentional Insider Threat |
|
| 328 | Incident Reporting |
|
| 329 | Phishing Websites |
|
| 330 | Open Wi-Fi Risks |
|
| 331 | Cloud Services |
|
| 332 | AI risks and best practices |
|
506 | Smartphones |
|
CYBER GAMES
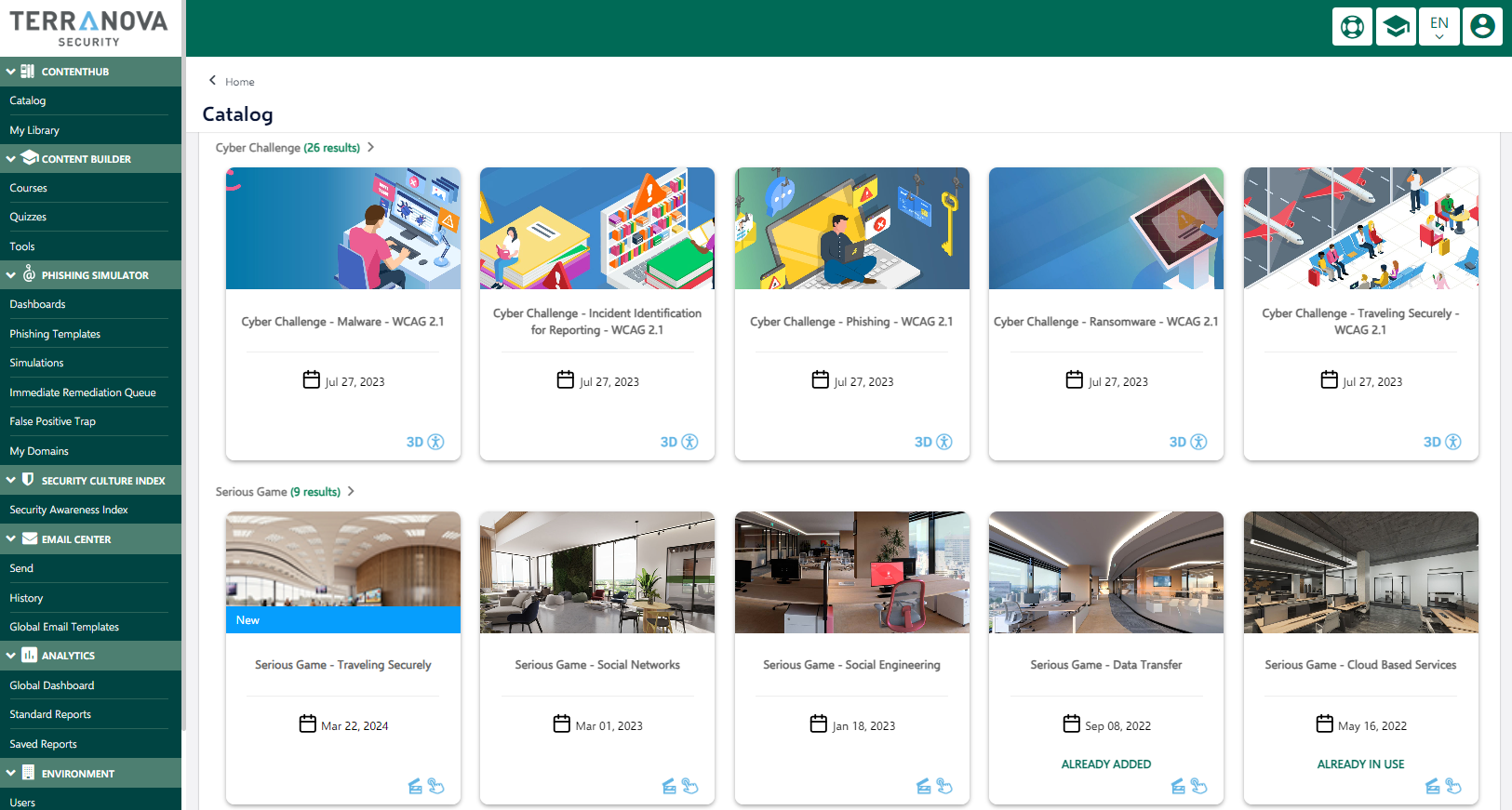
Cyber Game modules are interactive, gamified eLearning modules that reinforce fundamental cyber security best practices. Whether it’s a Serious Game that takes place in a 3D environment or a bite-sized Cyber Challenge, answer skill-testing questions, earn points for correct responses, and practice crucial cyber security decision-making in real-world scenarios.
Serious Game
Serious Game modules put end users in the middle of immersive, exciting scenarios that test their cyber security knowledge in a gaming-style environment. Each module focuses on a specific topic as players collect points and race against the clock to complete interactive learning activities.
- BEC
- Cloud Based Services
- Data Transfer
- Ransomware
- Securing the Home Office
- Social Engineering
- Social Networks
- Strong Password
- Traveling Securely
- Working Remotely
Cyber Challenge
Cyber challenges are engaging, gamified learning activities that test and reinforce fundamental security awareness knowledge on topics like phishing, email security, and more.
- Cloud Services
- Incident Identification for Reporting
- Information Classification
- Information Lifecycle
- Malware
- Mobile Devices
- Phishing
- Privacy
- Protecting Your Home Office
- Ransomware
- Social Engineering
- Traveling Securely
Serious Game
| Code | Topic | Description |
|---|---|---|
| 1 | Strong Password |
|
| 2 | Securing the Home Office |
|
| 3 | Ransomware |
|
| 4 | BEC |
|
| 5 | Cloud Based Services |
|
| 6 | Data Transfer |
|
| 7 | Social Engineering |
|
| 8 | Social Networks |
|
9 | Traveling Securely |
|
10 | Working Remotely |
|
Cyber Challenge
| Code | Topic | Description |
|---|---|---|
| 102 | Information Classification |
|
| 103 | information Lifecycle |
|
| 201 |
| |
| 205 | Social Engineering |
|
| 207 | Privacy |
|
| 210 | Phishing |
|
| 301 | Malware |
|
| 321 | Mobile Devices |
|
| 322 | Traveling Securely |
|
| 323 | Protecting Your Home Office |
|
| 324 | Ransomware |
|
| 328 | Incident Identification for Reporting |
|
| 331 | Cloud Services |
|
RISK-BASED
Microlearning
Built to increase employee knowledge retention and promote lasting behavioral change, microlearning modules feature concise training content. Each module targets specific risks and helps organizations meet productivity objectives.
- Access Control
- Applying the Clean Desk Principle
- Authentication method
- Business Email Compromised (BEC)
- C-Level Email Impersonation
- Cyber Quiz
- Friend or Foe?
- Handling Unidentified Individuals
- Mass Market Phishing
- OAuth consent grant
- Phishing by Phone
- Policy Tips Around Sensitive Information
- Ransomware
- How to Report Suspicious Messages
- Risky USB
- Securing the Home Office Environment
- Sharing an Organization Computer
- Smishing
- Spear Phishing
- Teams phishing
- Understanding App Consent Requests
- Unintentional Insider Threat
- Unsecured Sharing of Sensitive Documents
- Vishing
- Web Phishing
- Whaling
- Email Account Compromise
- Application Account Compromise
- Browser Compromise
- Computer Compromise
- Malicious Digital QR Codes
- Malicious Printed QR Codes
- AI: Helpful Tool or Threat?
- Deepfakes
| Code | Topic | Description |
|---|---|---|
| 3001 | Vishing |
|
| 3002 | Web Phishing |
|
| 3003 | Mass Marketing Phishing |
|
| 3004 | Spear Phishing |
|
| 3005 | Smishing |
|
| 3006 | Whaling |
|
| 3007 | C-Level Email Impersonation |
|
| 3008 | Business Email Compromise (BEC) |
|
| 3009 | Handling Unidentified Individuals |
|
| 3010 | Ransomware |
|
| 3011 | Unintentional Insider Threat |
|
| 3012 | Friend or Foe? |
|
| 3013 | Access Control |
|
| 3014 | Applying the Clean Desk Principle |
|
| 3015 | Risky USB |
|
| 3016 | Phishing by Phone |
|
| 3017 | Cyber Quiz |
|
| 3021 | How to Report Suspicious Messages |
|
| 3022 | Understanding App Consent Requests |
|
| 3023 | Unsecured Sharing of Sensitive Documents |
|
| 3024 | Sharing an Organization Computer |
|
| 3025 | Securing the Home Office Environment |
|
| 3026 | Policy Tips Around Sensitive Information |
|
| 3027 | Teams Phishing |
|
| 3028 | OAuth Consent Grant |
|
| 3029 | Authentication Method |
|
| 3030 | Email Account Compromise |
|
| 3031 | Application Account Compromise |
|
| 3032 | Browser Compromise |
|
| 3033 | Computer Compromise |
|
| 3034 | Malicious Digital QR Codes |
|
| 3035 | Malicious Printed QR Codes |
|
3037 | AI: Helpful Tool or Threat? |
|
3038 | Real or not? How deep is the fake? |
|
3039 | Secure Online Meetings |
|
3040 | Multichannel social engineering |
|
3043 | Supply Chain Attacks |
|
Nanolearning
Ideally suited for just-in-time training for phishing simulation clickers or as short standalone eLearning opportunities, nanolearning modules ensure end users understand specific cyber security fundamentals. Each module walks users through risks, consequences, and best practices related to a given topic.
- Anatomy of a Spear Phishing Attack
- Being Security Aware
- Cloud-Based Sharing
- Credential Theft
- Cyber Attack Detection
- Identity Theft - Example of an Attack
- Double Barrel Phishing Attack
- Insider Threat
- Phishing - Six Clues That Should Raise Your Suspicions
- Phishing Website
- Preventing Security Breaches
- Protecting Sensitive Information - Information Handling
- Ransomware
- Smishing
- Social Engineering Techniques and How to Spot Them
- Social Engineering via Email
- The Risks of Social Networks
- Spear Phishing - The CEO Fraud
- Spoofing
- Stegosploit
- Vishing
- Web Conferences Risks
- Wi-Fi Security
- What is two-factor authentication
| Code | Topic | Description |
|---|---|---|
| 2001 | Ransomware |
|
| 2002 | Vishing |
|
| 2003 | Phishing - Six Clues |
|
| 2006 | Protecting Sensitive Information |
|
| 2007 | Cyber Attack Detection |
|
| 2008 | Preventing Security Breaches |
|
| 2010 | Protecting your information from Wi-Fi security risks |
|
| 2011 | Identity Theft |
|
| 2013 | Social engineering techniques and how to recognize them |
|
| 2015 | Being Security Aware |
|
| 2016 | Spear Phishing CEO Fraud |
|
| 2025 | Phishing Website |
|
| 2026 | The Risks of Social Networks |
|
| 2035 | Smishing |
|
| 2050 | Anatomy of a Spear Phishing Attack |
|
| 2051 | Insider Threats |
|
| 2052 | Social Engineering via Email |
|
| 2053 | Spoofing: How to avoid becoming a victim |
|
| 2054 | Double Barrel Phishing Attack |
|
| 2055 | Stegosploit |
|
| 2056 | Web Conferences Risks |
|
| 2057 | Cloud-Based Sharing |
|
| 2058 | What is multi-factor authentication |
|
2059 | Understanding deepfakes |
|
Nanovideo
Ideally suited for just-in-time training for phishing simulation clickers or as short standalone video-based eLearning, nanovideo modules showcases the risks, consequences, and best practices related to a given topic.
- Browser-in-the-browser Attack
- Credential Theft
- Cyber Fraud
- Employee Data Breach
- Countering Misinformation: The Power of Critical Thinking
- Financial Data Exposure
- Generative AI: What is it? Risks and Benefits
- Identity Theft
- Importance of Security Culture in the Organization
- Malicious Software
- Ransomware
- Website URL
| Code | Topic | Description |
|---|---|---|
| 4 | Ransomware |
|
| 5 | Website URL |
|
| 6 | Credential Theft |
|
| 7 | Identity Theft |
|
| 8 | Financial Data Exposure |
|
| 9 | Cyber Fraud |
|
| 10 | Employee Data Breach |
|
| 11 | Malicious Software |
|
| 12 | Importance of Security Culture in the Organization |
|
13 | Browser-in-the-browser Attack |
|
14 | Generative AI: What is it? Risks and Benefits |
|
15 | Countering Misinformation: The Power of Critical Thinking |
|
16 | Risks associated with file transfer |
|
17 | Spotting a suspicious sender |
|
24 | Detecting and preventing credit card fraud |
|
ROLE-BASED
Constructed to appeal to various context-specific security awareness best practices, each role-based explores the cyber security roles and responsibilities related to different functions with an organization. Fortra offers role-based courses for professionals in finance, human resources, executives, and much more.
Information Security Awareness for:
- Executives
- Introduction to Information Security
- Passwords
- Phishing
- Confidentiality on the Web
- Mobile Devices
- Data Leakage
- Business Email Compromise
- Finance
- Introduction to Information Security
- Passwords
- Phishing
- Confidentiality on the Web
- Protecting Payment Card Data
- Data Leakage
- Help Desk
- Introduction to Information Security
- Passwords
- Access Control
- Social Engineering
- Phishing
- Incident Reporting
- Human Resources
- Introduction to Information Security
- Passwords
- Phishing
- Confidentiality on the Web
- Privacy
- Data Leakage
- IT Administrators
- Network Security Overview
- Common Network Attacks
- Securing Networks
- Securing Data Repositories
- IT Developers
- Application Security Overview
- Common Application Attacks
- Secure Development
- Cryptography Overview
- Access Control
- IT Privileged Users
- Introduction to Information Security
- Passwords
- Access Control
- Phishing
- Malware
- Ransomware
- Unintentional Insider Threat
- Incident Reporting
- Working Remotely
- Managers
- Security Challenges
- Security Governance
- Leading by Example
- OWASP
- Open Web Application Security Project (OWASP)
| Code | Topic | Description |
|---|---|---|
| FIN | Finance |
|
| GEST | Managers |
|
| HR | Human Resources |
|
| TIA | IT Administrators |
|
| TID | IT Developers |
|
| EXEC | Executives |
|
| PRIT | IT Privileged Users |
|
| HD | Help Desk |
|
OWASP
| Code | Topic | Description |
|---|---|---|
| OWASP | Open Web Application Security Project (OWASP) |
|
COMPLIANCE & PRIVACY
Ensuring that all organizations can easily understand and comply with various data privacy regulations, this course provides high-quality training content and activities exploring key data protection trends.
- CCPA Essentials
- GDPR Essentials
- HIPAA/HITECH
- Personal information protection in the private sector in Quebec
- Key aspects of the reform
- Companies’ obligations
- Default protection of personal information
- Individuals’ rights, and how to protect their information
- Personally Identifiable Information (PII)
- PCI DSS Awareness
- POPI Act
- Privacy Essentials
- The Protection of Personal Data
- Collecting Personal Data
- Privacy Principles
- Privacy Breaches
- Protected Health Information (PHI)
- Protected Health Information for Europe
- Security by Design (SBD)
- Introduction to Digital Operational Resilience Act (DORA)
- Introduction to NIS2 Directive (NIS2)
| Code | Topic | Description |
|---|---|---|
| 801 | Personally Identifiable Information (PII) |
|
| 803 | Protected Health Information (PHI) |
|
| 818 | GDPR Essentials |
|
| 819 | CCPA Essentials |
|
| 820 to 823 | Privacy Essentials |
|
| 830 to 833 | Personal information protection in the private sector in Quebec |
|
| 840 | Protected Health Information for Europe |
|
| HIPAA/HITECH | HIPAA/HITECH |
|
| PCI | PCI DSS Awareness |
|
| POPIA | POPI Act |
|
| SBD | Security by Design (SBD) |
|
| DORA | Introduction to Digital Operational Resilience Act |
|
| NIS2 | Introduction to NIS2 Directive |
|
| NIST | Introduction to NIST Cybersecurity Framework |
|
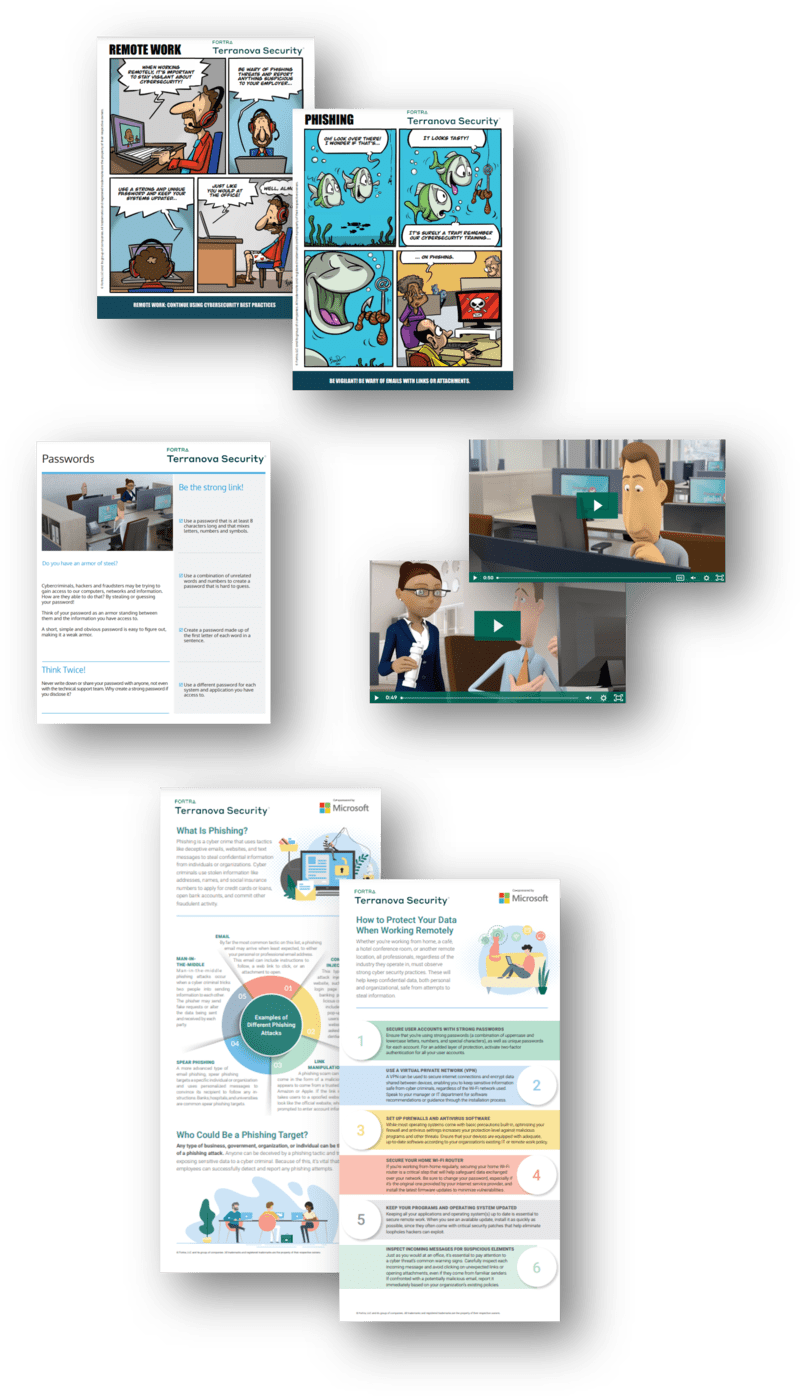
Communication & Reinforcement Tools
Increase employee engagement with a diverse suite of communication tools, with new assets added regularly
Newsletters
Send training updates and security best practice highlights directly to your users.
Posters
Promote your training program with visuals you can tailor to match your brand.
Wallpapers and Web Banners
Increase program engagement with vivid, thought-provoking digital messaging.
Comics
Add a fun visual aspect to your training program with short comics depicting characters in relatable scenarios.
Infographics
Share cyber security tips and best practices in a compact, engaging format that’s perfect for social or intranets.
Cyberpedia
Get everything you need to know about key cyber security topics in exhaustive, informative webpages.
What Is Videos
Send cyber security tips and best practices to users in bite-sized streaming video format. View sample videos >
All communication tools are currently available in EN, FR-CA, FR-FR, and ES LATAM. For additional language support, please contact the Fortra Customer Success team.