Phishing is a cyber-attack that uses fraudulent emails, websites, and text messages to convince victims to give up personal information and corporate data.
The motivations behind phishing are varied and include identity theft, unauthorized access to computer systems, or direct financial gain through fake invoices.
Hackers who rely on phishing use tactics like fear, urgency, and semblance of authority to make their victims forget or skip common security measures. Not only is phishing prevalent, but it’s also becoming increasingly sophisticated and harder to spot.
In Terranova Security’s most recent Gone Phishing Tournament, a free annual phishing simulation training event, 1 in 10 end users were found to be susceptible to phishing attacks.
Phishing is a varied and rapidly evolving cyber threat. With new versions popping up with the help of AI, the only true protection against this hack is through human risk management.
7 Common Types of Phishing Attacks
Phishing is based on the concept of deception. Most modern technologies and communication channels can be exploited to launch phishing attacks, such as:
This is the most common phishing delivery method. An email is sent to multiple recipients urging them to update personal information, verify account details, or change passwords.
These emails are expertly crafted to drive a sense of urgency in their victims. Whether the criminal asks for personal information, a login reset to steal a password, or brazenly asks for a false invoice to be signed, phishing emails always request the task be done as soon as possible to push the victim to execute the task without thinking twice.
Content Injection
This hack relies on cracking an existing popular website to inject a small tidbit of code on the page. This code then enables a pop-up, form or link directing people to a secondary website to steal their personal information.
CEO Fraud
These attacks focus on sounding like urgent requests from the company's CEO. These hackers often have a lot of information about the company.
They will have acquired knowledge such as colleagues' names, company milestones, and even departmental organization in order to sound more believable. These attacks often come near the end of the day, with a request needing to be completed before EOD.
Website Spoofing
Hackers use replicas of high-traffic websites, such as social media or banking websites, to fool users into inputting their credentials and stealing their identity and funds. Using this tactic, hackers often hire professional designers who can replicate the institution’s website to a tee.
Mobile Phishing
These attacks boast the same tactics as regular phishing attacks but are led by text messages and social media in-app messages.
Sender information is easier to fake on these platforms, making phishing attacks harder to detect compared to email, where a simple domain check thwarts a large portion of attacks.
Spear Phishing
Spear phishing is advanced targeted email phishing, often being sent one by one after extensive research on the victim. Examples of spear phishing include infiltrating a hospital, bank, or university to steal data that severely compromises the organization.
Voice Phishing
Vishing relies on automated robocalls to send millions of fake calls to potential victims. During these calls, victims are made to believe they owe money to the government or on an old loan. Even the voicemails left by these hackers can retrigger the scam.
Did you know?
Social engineering and phishing are successful because they rely on the natural human tendency to trust others. People assume the password update or wire transfer request is legitimate because they recognize the source and believe they are acting in the best interests of themselves and others.
What Is a Phishing Simulation?
Phishing simulations are real-life phishing emails that organizations can send to their employees to assess their online behaviors and understanding of phishing threats. These simulated emails are concocted from actual trends seen in criminal phishing emails to test employee readiness.
These simulations equip employees with the required skills to detect, identify and evade certain cyber threats. They also provide helpful data to companies about potential knowledge gaps within their workforce.
Phishing, social engineering and ransomware can all be thwarted through cyber security awareness. However, since these threats evolve rapidly, regular phishing simulations are required to keep employees ahead of the game.
What is Trap Phishing?
Trap phishing typically preys on security vulnerabilities in common online behavior. Such habits can include completing online transactions, sharing information on social media, and more. Trap phishing schemes lure unsuspecting users to a malicious webpage by posing as a legitimate organization or familiar business.
Often interpolating recognized branding or vocabulary, victims are enticed to click on a phishing email link and/or provide sensitive information via the malicious webpage. Though not as targeted as other phishing scams, these generic attacks can still be quite effective.
How Does Phishing Happen?
Phishing happens when an unsuspecting victim responds to fraudulent requests that demand action. This action can include downloading an attachment, clicking a link, filling out a form, updating a password, calling a phone number, or using a new Wi-Fi hotspot.
A crucial aspect of successful security awareness training is educating people about how easy it is to be tricked into giving up confidential information.
The following examples of phishing underscore how easy it is for anyone to be a victim of phishing.
6 Clues That You Are A Target Of A Phishing Email
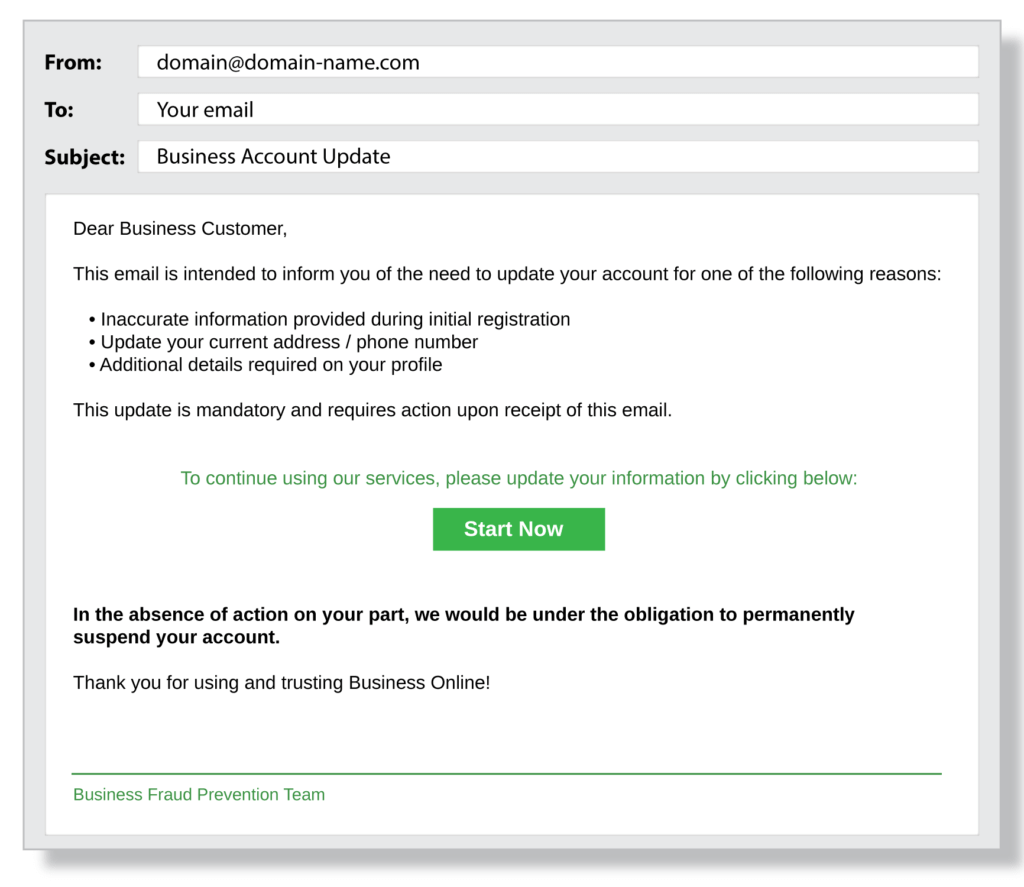
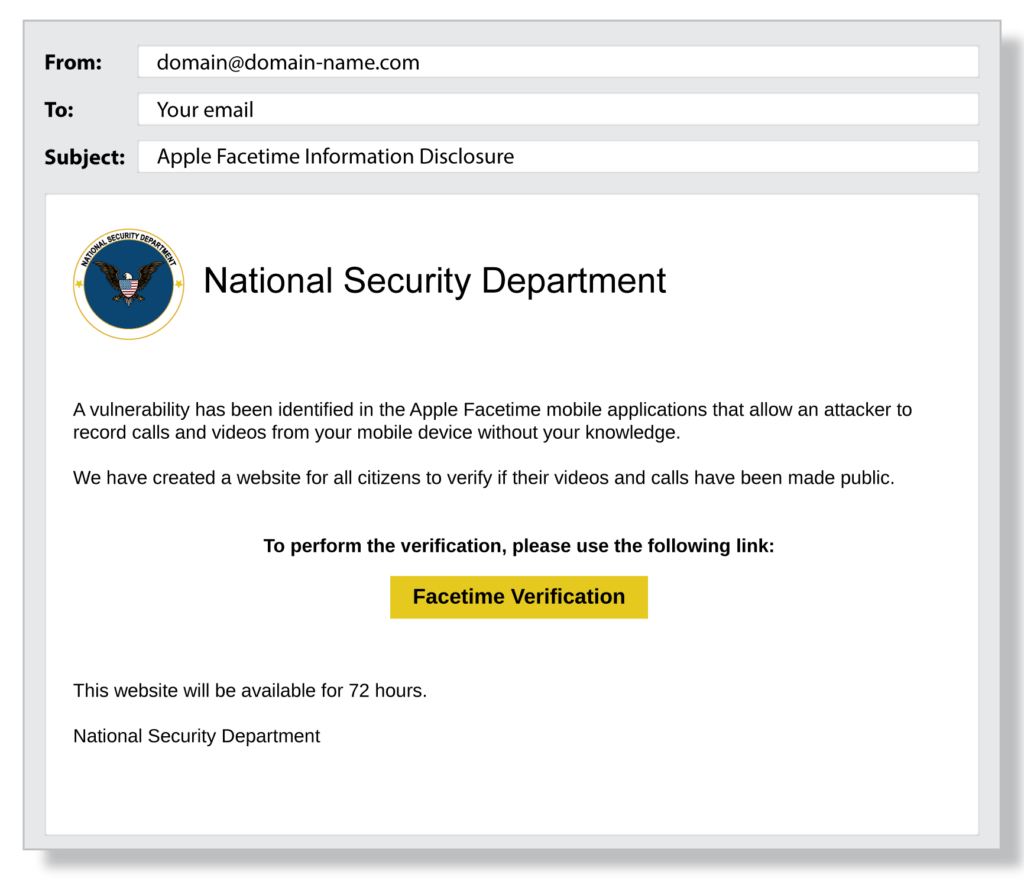
Sender
Sender
Just because you know the person whose name is on the email doesn't make it safe.
A name is easy to fake.
Check the email address to confirm that the email is really from that person.
Salutation
Salutation
Take a good look at the salutation.
If it says "Dear client," "Dear Customer" or "Dear Valued Customer," instead of your name, beware!
Content
Content
Scammers try to create a sense of urgency so that you act rather that think (e.g., your account will be blocked!).
Poor grammar and spelling mistakes? No legitimate organization would ever let such mistakes get by it.
They ask you for personal or financial information.
They ask you to update your account or change your password. But you won't fall for that!
Report anything that seems suspicious to your IT service desk.
Link or Button
Link or Button
Emails usually try to get you to click a link or button, which takes you to a fake website or installs malware.
Unless you can confirm the sender's identity, you should never click.
Attachment
Attachment
When you open a scammer's attachment, you open the door to malware.
Malware can wreak havoc on your computer or even your organization's entire network.
Contact Information
Contact Information
Legitimate organizations want you to get in touch with them, if necessary.
They show their contact information in their email so you can call them and verify that they are who they say they are.
Try to spot the clues in the following examples of phishing emails:
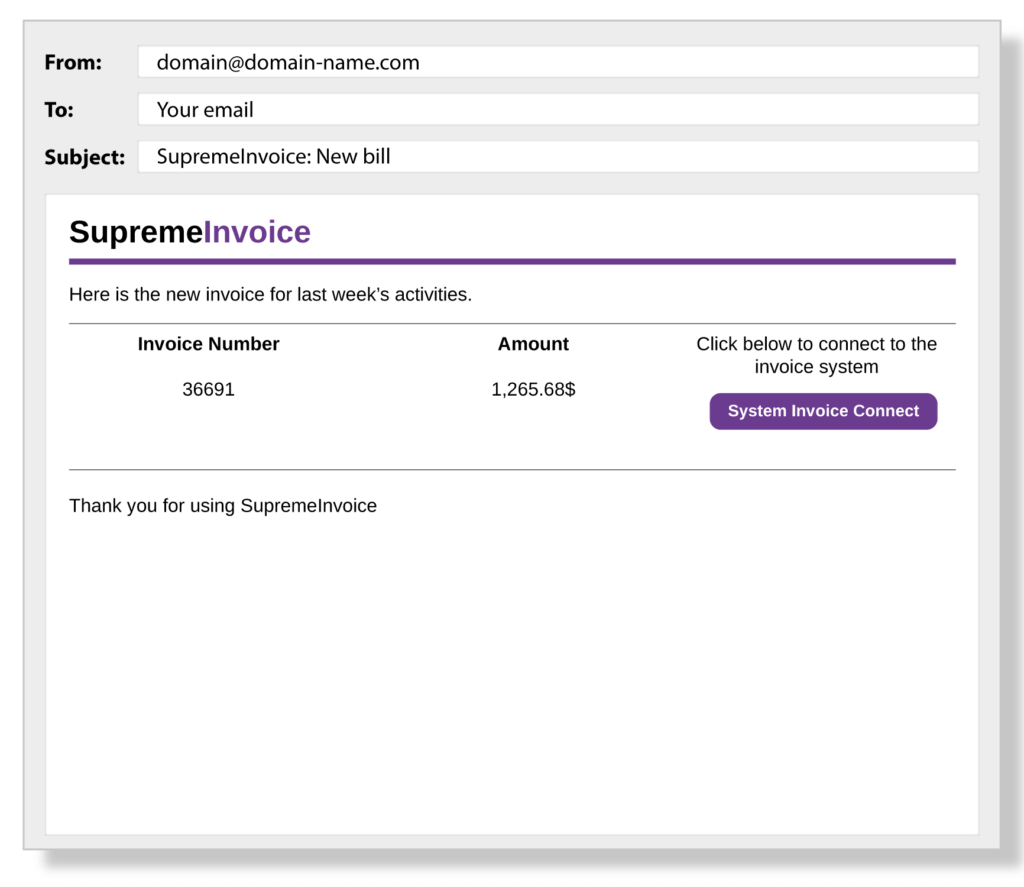
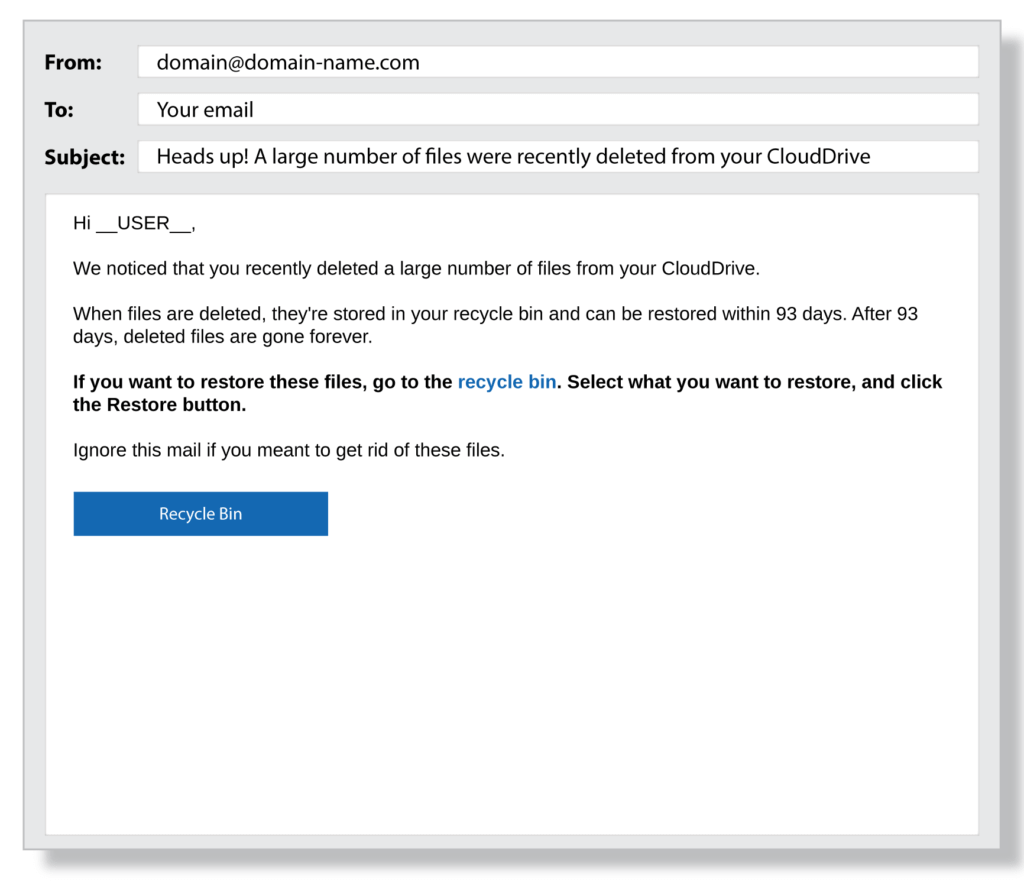
How to Prevent Phishing
To help prevent phishing, Terranova Security recommends taking the following precautions:
 Educate your employees about phishing. Take advantage of free phishing simulation tools to educate and identify phishing risks.
Educate your employees about phishing. Take advantage of free phishing simulation tools to educate and identify phishing risks.
 Use proven human risk management and phishing simulation platforms to keep employees' phishing and social engineering risks top of mind. Create internal cybersecurity heroes committed to keeping your organization cyber secure.
Use proven human risk management and phishing simulation platforms to keep employees' phishing and social engineering risks top of mind. Create internal cybersecurity heroes committed to keeping your organization cyber secure.
 Remind your security leaders and cybersecurity heroes to regularly monitor employee phishing awareness with phishing simulation tools. Use phishing microlearning modules to educate, train, and change behavior.
Remind your security leaders and cybersecurity heroes to regularly monitor employee phishing awareness with phishing simulation tools. Use phishing microlearning modules to educate, train, and change behavior.
 Provide ongoing communication and campaigns about cyber security and phishing. This includes establishing strong password policies and reminding employees about the risks that can come in the format of attachments, emails and URLs.
Provide ongoing communication and campaigns about cyber security and phishing. This includes establishing strong password policies and reminding employees about the risks that can come in the format of attachments, emails and URLs.
 Establish network access rules that limit the use of personal devices and the sharing of information outside of your corporate network.
Establish network access rules that limit the use of personal devices and the sharing of information outside of your corporate network.
 Ensure that all applications, operating systems, network tools, and internal software are up-to-date and secure. Install malware protection and anti-spam software.
Ensure that all applications, operating systems, network tools, and internal software are up-to-date and secure. Install malware protection and anti-spam software.
 Incorporate cyber security awareness campaigns, training, support and education into your corporate culture.
Incorporate cyber security awareness campaigns, training, support and education into your corporate culture.
Did you know?
Phishing simulations allow you to identify which employees are prone to phishing and educate your team on how easy it is for phishing to happen.
What is Phishing Training?
Phishing training or simulation is the most efficient way to raise awareness of phishing risks and identify which employees are at risk for phishing.
Phishing simulations allow you to incorporate cyber security awareness into your organization in an interactive and informative format.
Real-time phishing training are a fast and effective way to educate your users and increase alertness levels to phishing attacks. People see first-hand how CEO fraud, emails, fake websites, malware and spear phishing are used to steal personal and corporate information.
Top 10 Benefits of a Phishing Simulation
Phishing simulations are an essential tool in any corporate cybersecurity strategy. These tests provide real-world experience to employees, allowing them to detect phishing attempts in a safe space. Phishing simulation also provides the following benefits:
1. Assess corporate and employee cybersecurity readiness
2. Greatly diminish the number of successful phishing attempts
3. Refresh users’ minds about new phishing tactics.
4. Build a cybersecurity culture that recognizes and celebrates cybersecurity heroes
5. Modify behavior to correct the automatic trust reflex
6. Gain the ability to launch personalized anti-phishing programs
7. Safeguard critical corporate data and employee personal information.
8. Fulfill regulatory compliance in your industry.
9. Measure the success of your cyber security awareness training.
10. Test each department with different variations of phishing emails to identify gaps.
Phishing Awareness Training
From fraudulent shipping confirmation messages to suspicious gift card and refund offers, Terranova Security phishing templates replicate real-life attacks that can occur at any time.