Most skilled cyber attackers don't need exploits to access an enterprise network. In many examples of Business Email Compromise (BEC) attacks, all it takes is a simple phishing scam to trick the user into handing over their login credentials.
In these attacks, a hacker sends an employee a phishing email posing as a trusted individual to trick the victim into handing over sensitive information about the business, sending money, or sharing intellectual property.
Research shows that BEC attacks increased by more than 81% over the past year and 175% over the last two years. They began targeting smaller companies, with a 145% increase in malicious emails targeting SMBs.
Let's examine how these scams work, review five examples of BEC attacks, and focus on how to protect your organization.
How Most BEC Attacks Work
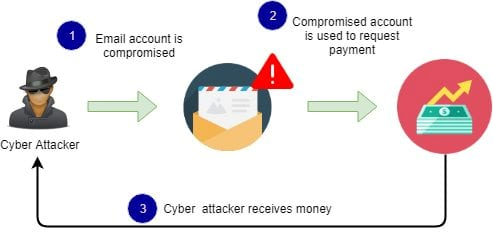
Source: Infosec Institute
Generally, a BEC attack begins when a cybercriminal gathers intelligence on a target business. During this phase, the criminal collects publicly available information about company personnel (such as names and titles) from news releases, social media accounts, and website content.
Using this information, the cybercriminal then attempts to gain access to the business email system with a phishing email or spoof the email account of a key employee.
After gaining email access, the attacker sends targeted, high-pressure emails to employees to trick them into handing over protected information.
This tactic often works because the employee sees the email is from a trusted individual and doesn't think twice about handing over information or funds.
Part of the challenge with mitigating these threats is that most employees don't know how to spot phishing scams. According to the Gone Phishing Tournament Report, 44% of employees click email phishing links.
5 Examples of Business Email Compromise
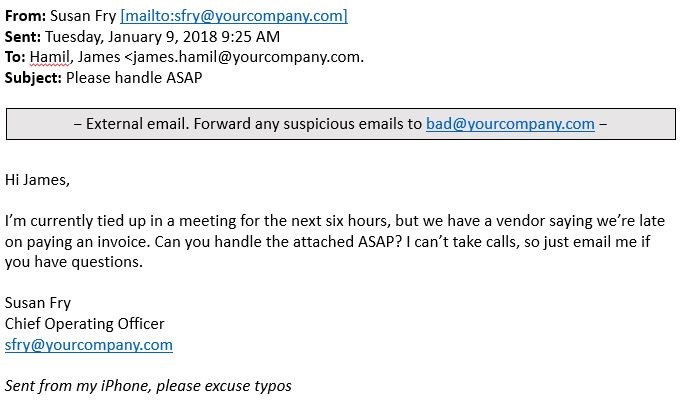
Example of a bogus invoice. Source: PhishLabs
Most attackers use some variation of five examples of business email compromise. These include:
1. Bogus invoice schemes
In these scams, a cybercriminal takes over or spoofs an employee's email account authorized to process invoice payments and fund transfers. The attacker then uses this account to ask another employee to transfer the funds or pay an invoice to the fraudster's account.
2. CEO fraud
A cybercriminal steals or spoofs an executive's email account and uses this to trick other users into giving up sensitive information or money. The hacker emails the victim requesting a money transfer.
3. Account Compromise
One of the most common BEC attacks is where the hacker obtains access before mining the employee's contact list for company vendors, partners, and suppliers. The attacker then messages these contacts requesting payments be sent to a fake account.
4. Attorney impersonation
Sometimes hackers go as far as impersonating an organization's attorney to contact company employees or the CEO and request funds. Skilled attackers usually do this on Friday afternoons or before the holidays when workers rush to get things done and don't question the details.
5. Data theft
Intruders often take over the business email of one or more HR staff so they can send requests for confidential information about employees, partners, and investors. The hacker later uses this data as part of a wider BEC or cyberattack against the business.
How to Recognize Business Email Compromise Attacks
BEC attacks can take various forms, but they are often identifiable by following a common format:
- Spoofed sender domain
- Contains typos and grammatical errors
- Urgency in the email subject and body
- Requests for a fund transfer
- The sender is an influential person in the business
How to Prevent BEC Attacks
Security leaders can take some simple steps to thwart BEC attacks:
1. Raising awareness of examples of BEC attacks
Educate your employees about the five types of BEC attacks. Use phishing simulations to teach employees how to identify BEC and phishing attempts.
2. Conduct regular security awareness training
Provide employees with regular security awareness training and phishing simulations to keep BEC and social engineering risks top of mind. Name internal cybersecurity heroes committed to keeping your organization secure.
3. Monitor employee awareness
Encourage security leaders and cybersecurity heroes to monitor employees' BEC and phishing awareness with regular phishing simulations. Use microlearning modules to educate, train, and change employees' behavior toward cybersecurity best practices.
4. Send ongoing communications about threats
Provide employees with constant communication and campaigns about cybersecurity, BEC, and social engineering. This includes establishing strong password policies and reminding employees about the risks of emails, URLs, and attachments.
5. Set network access rules
Establish network access rules to limit personal device use and prevent information sharing outside the network's perimeter.
6. Update all infrastructure
Ensure all applications, operating systems, network tools, and internal software are up-to-date and secure. Install malware and anti-spam software.
BEC Prevention Starts with Your Employees
Like all cyber threats that rely on manipulation, it only takes one employee to make a misguided decision — such as clicking on a malicious link or sharing personal information — to trigger a data breach that can affect your entire organization.
By alerting employees to common examples of business email compromise attacks, you empower them to recognize manipulative phishing emails. This proactive approach significantly reduces the likelihood of attackers deceiving your users into divulging sensitive information.
Ready to enhance your organization's security awareness training? Schedule a demo to see how to break the attack chain.
Protect Your Company from BEC Attacks
Protect yourself from BEC attacks by training your employees to identify and prevent them. Conduct a regular phishing simulation to determine your company's cyber security resilience.