Interactive, Role-Based Content Library
Help employees understand the scope of the General Data Protection Regulation (GDPR) training requirements as well as the associated rights and responsibilities.
- The GDPR requires that your employees be trained and knowledgeable (articles 39 and 47).
- The EU regulation applies to all organizations processing the personal information of EU data subjects, regardless of where they are located in the world.
- Failure to comply with GDPR may result in serious fines and reputation risks.
The GDPR training solution helps educate your staff on how to better protect personal information and reinforce learning to maximize behavior change.
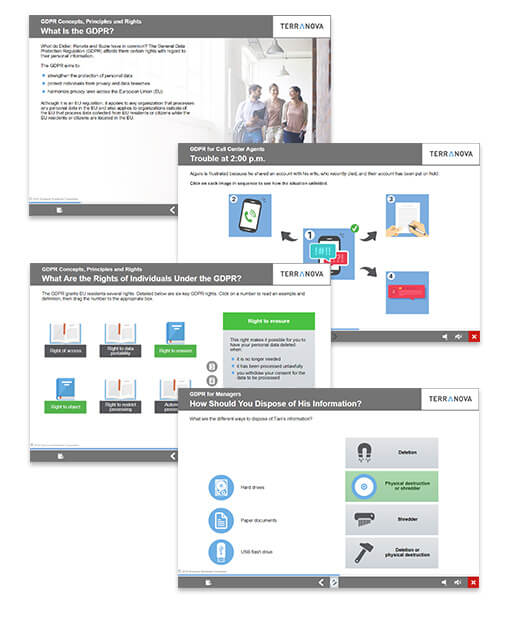
GDPR Essentials
GDPR Essentials
Time: 15 min.
The learning objective of this awareness course is to introduce you to the General Data Protection Regulation, known as the GDPR, as well as help you understand how the GDPR may affect some of your daily activities.
Topics:
- The key components of this privacy regulation
- The rights granted to European residents and citizens
- The rules that businesses and organizations must follow
GDPR for Procurement Employees
GDPR for Procurement Employees
Time: 20 min.
This course will explain how to apply GDPR principles to procurement.
Topics include
- how to amend contracts that are not GDPR compliant
- how to apply these principles to all third-party contracts involving EU personal data, whether those contracts are with companies or individual consultants
GDPR TRAINING MODULE - SEE IT IN ACTION
Learn how to effectively manage personal data and comply with GDPR training requirements.
Easily and Quickly comply with GDPR Training Requirements!
Additional Resources for Security Professionals

Discover the power of personalized reporting
Learn about data-driven insights, how they improve security awareness training decision-making, and how they bolster your ROI.

How to Protect Your Data from Social Engineering
Learn how to detect common social engineering tactics and threats and protect confidential data from cybercriminals.
Your Communication Tools
Adaptive. Engaging. Sharp.
Imagine the right communication strategy for your GDPR campaign. Imagine the right tools that effectively engage audiences while adapting to your organization and facilitating successful collaborations among employees.
Now imagine all this, just in time.
Your Communication Toolbox

A complete suite of communication tools that features relevant topics in GDPR. Content and visual designs are updated regularly as to reflect ongoing trends in the cyber risk landscape.
Objectives:
- Raise security awareness
- Mobilize your workforce
- Promote new and existing campaigns
- Reinforce learned concepts and skills


