
Identity theft occurs when criminals steal a victim's personal information to commit criminal acts. Using this stolen information, a criminal takes over the victim's identity and conducts a range of fraudulent activities in their name.
Cyber criminals commit identity theft by using sophisticated cyber attack tactics, including social engineering, phishing, and malware. Identity theft can also result from rudimentary tactics with criminals stealing mail, digging through dumpsters, and listening in on phone conversations in public places.
The ultimate goal of many cyber attacks is to steal enough information about a victim to assume their identity to commit fraudulent activity. Unfortunately, most people only discover they're victims of identity theft when they apply for a loan, attempt to open a bank account, apply for a job, receive a call from a collection agency, or request a new credit card.
Cyber criminals prey on corporations, schools, government agencies, hospitals, and other institutions that hold employees' personal information. Because of this, the damage done by identity theft is far-reaching. Cyber criminals hope an employee with access to personal information clicks a link in a phishing email, opening up access to databases of personal and financial information.
Damage done by identity theft has a trickle-down effect, causing personal and emotional trauma for the person who accidentally gives the cyber criminal access to data. There are also severe consequences for the people whose personal information is stolen and the violated organization's reputation.
Types of Identity Theft
There are generally three types of identity theft: financial, medical, and online. These are categorized according to the platform that cyber criminals use your stolen information in.
How Serious Is Identity Theft?
Identity theft is a worldwide threat. Many governments have programs in place to help their citizens report identity theft and establish a recovery plan:
1. In Canada, contact the Canadian Anti-Fraud Call Centre at 1-888-495-8501.
2. In the United States, contact the Federal Trade Commission at 1-877-438-4338.
3. In other counties, check your government's website for information.
A recent IBM report reveals that, on average, a data breach resulting in identity theft costs the violated organization $4.35 million. It typically takes 277 days to realize a data breach has happened.
Because identity theft is so serious, it’s important that every employee in your organization knows how to spot and protect themselves against this threat. This starts with a robust training system that aims to foster a culture of cyber security awareness.
The Cyber Security Hub
Sign up to access exclusive cyber security content. Get instant access to engaging, instantly shareable cyber security awareness content in multiple formats.
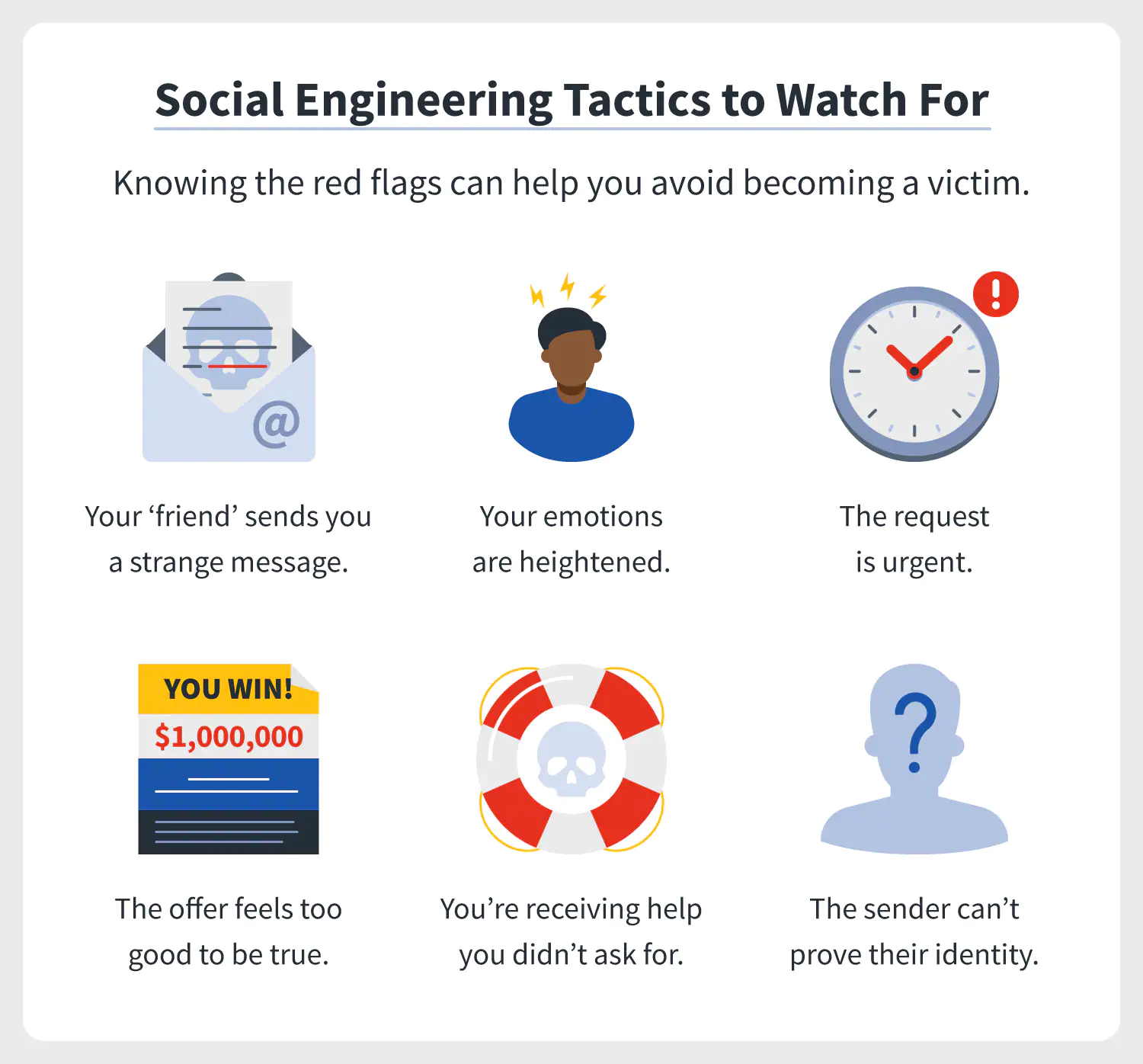
What is the Difference Between Social Engineering and Identity Theft?
Source: Norton
![]()
Identity theft and social engineering are tightly intertwined. In fact, the latter is a means to carry out identity theft and trick people into divulging important information.
![]()
Social engineering, which is the act of manipulating people to give up confidential information, relies on the basic human instinct of trust, greed, curiosity, and desire. And when used for ulterior motives, can quickly lead to sharing information that puts a person at risk.
How Does Identity Theft Happen?
1. Social engineering with an email, text, or phone message. All it takes is one downloaded file or a clicked link in an email or text message to open a gateway to sensitive information.
2. Malware such as installing spyware or keyloggers on the network. Criminals use spyware and keyloggers to track your keyboard and online activity to capture passwords, usernames, and other sensitive information.
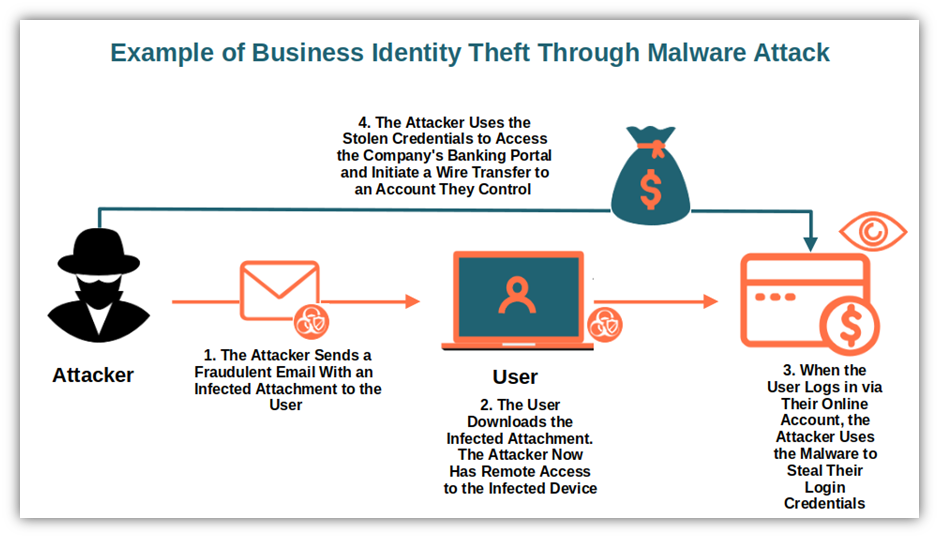
Source: Savvy Security
3. Researching social network sites for personal information, email addresses, employee connections, recent conferences, promotions, etc. Cyber criminals use this information to connect and familiarize themselves with their emails, texts, social media messages, or phone messages – convincing victims to respond.
4. Hacking computers and databases through a range of tactics. From fake websites used to steal passwords, attachments that install ransomware, vulnerabilities in systems, or fake wi-fi access points give access to personal information – cyber criminals have a deep range of hacking tactics.
5. Eavesdropping on telephone conversations in public places, the office building's lobby, on the bus, etc. All it takes is overhearing credit card and address details to have enough information to commit identity theft.
6. Retrieving paper documents from mailboxes, recycling bins, or trash cans and using this information to commit identity theft or additional cyber attacks such as spear phishing or business email compromise.
7. Creating fake online profiles convincing employees who do their due diligence on an unknown caller or email sender that the person is legitimate and can be trusted.
Identity Theft Facts
As of 2023, there have been 1.4 million FTC reports on identity theft, with total losses estimated to be $10.2 billion.
1 in 15 people experience some form of identity theft.
The most common victim of identity theft are millennials aged 30-39. However, there have been a number of cases involving loans and lines of credit in the name of 8-year-old children, costing families $1 billion yearly.
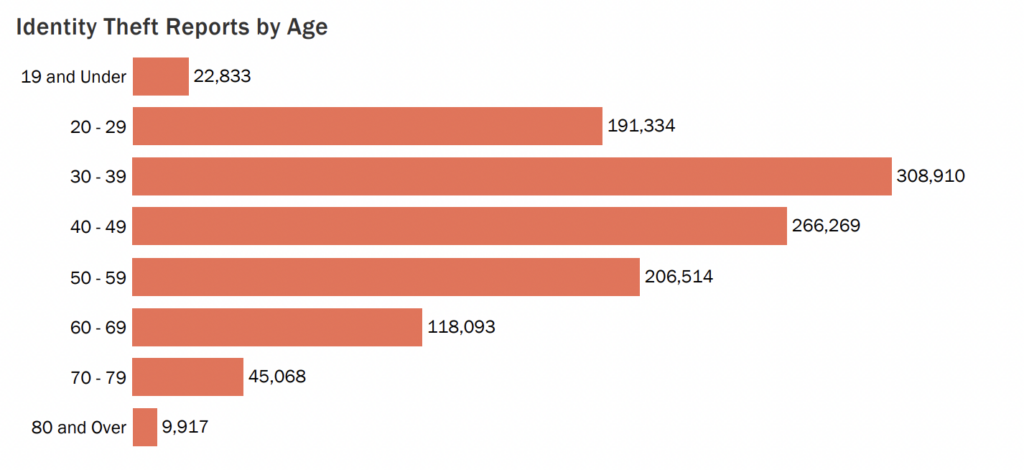
Source: IdentityTheft.org
- Americans are 50% more likely to be victims of identity theft, with numbers doubling the global average.
- Victims of identity theft are left with out-of-pocket losses amounting to $1.7 billion.
- People with social media accounts are 46% more likely to become victims of identity theft.
How Do Cyber Criminals Use Stolen Identities?
Cyber criminals use stolen identities to:
- Accumulate credit card charges on the victim's card.
- Get a new loan or line of credit in the victim's name.
- Transfer funds out of the victim's account without the victim noticing.
- Sign a lease in the victim's name.
- Collect government benefits owed to the victim.
- Submit fraudulent insurance claims in the victim's name.
- Obtain identification or travel documents.
- Apply for jobs, university/college, or grants and bursaries.
- Change usernames and passwords, locking the victim out of their accounts.
- Send phishing, vishing, or smishing attacks to people known to the identity theft victim.
- Hide criminal activities behind the victim's name.
How To Prevent Identity Theft
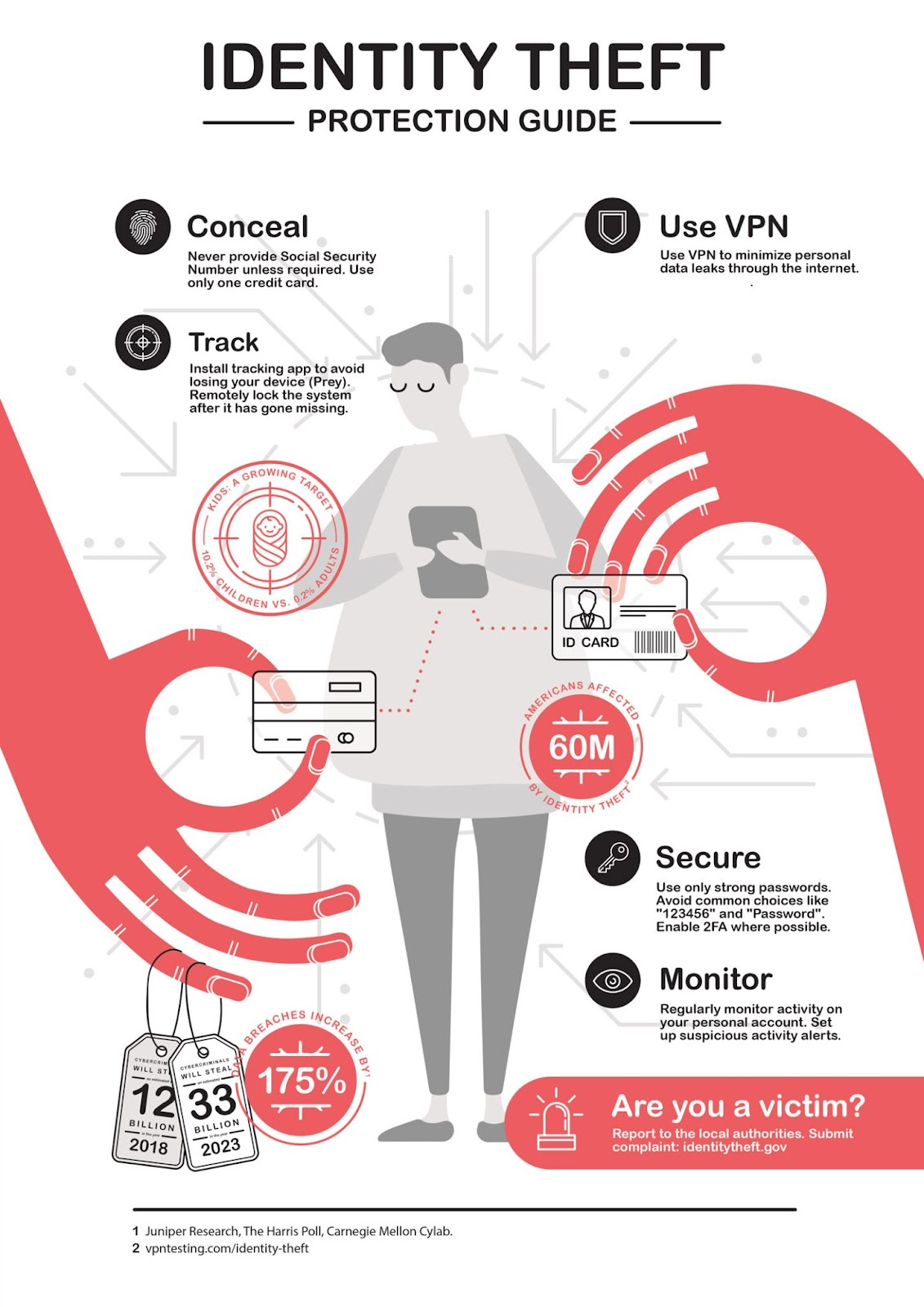
Source: Infographic Journal
To protect your employees and organization from identity theft, remind your employees of these cyber security best practices:
1. Do not provide confidential personal or corporate information over the phone or on a website unless you are sure of the recipient's credibility.
2. Make sure websites hosting online forms use https:// and have a padlock icon in the URL field. This prefix indicates the website is secure.
3. Choose strong passwords to protect access to your online accounts and change your passwords regularly. When possible, enable two-factor authentication.
4. Limit the amount of personal information you share on social networks. Cyber criminals use sites like LinkedIn, Twitter, Instagram, and Facebook to learn details about you and your employer and use this to trick you into trusting them.
5. Never write down your PIN or passwords.
6. Securely dispose of and shred documents containing personal, company, and confidential information. Do not store these documents in an easily accessible location.
7. Always verify a caller's identity before providing information over the phone. Do not be shy about asking the caller multiple questions to confirm their identity.
8. When in doubt, delete the email or text message and do not answer phone calls from unknown numbers and callers.
9. Do not provide personal information to people acting as pollsters or representing government organizations.
10. Never provide your date of birth, postal address, mother's maiden name, salary, or academic credentials to unsolicited callers, texters, or email senders.

What is Phishing Simulation?
Phishing simulation is vital in raising awareness of how identity theft happens. Phishing is one of the primary cyber attack tactics used by cyber criminals to access personal and confidential information.
Phishing simulations help you monitor phishing tactics and identify employees who are at risk of cybercrimes relying on social engineering.
Real-time phishing simulations are a fast and effective way to educate people and increase alertness levels of phishing and other cyber attack tactics. People see first-hand how their actions can put them at risk for identity theft and identity fraud.
How Can Phishing Simulations Help Prevent Identity Theft?
Your employees are your organization's first line of defense against data breaches and hacks, identity theft, and identity fraud.
Phishing simulations are key in giving employees the skills and knowledge needed to recognize cyber attack tactics and protect themselves and their organization from identity theft.
Phishing simulations help prevent identity theft with these primary benefits:
1. Measure the corporate and employee cyber threat risk level.
2. Reduce the cyber threat risk level.
3. Increase awareness of phishing, social engineering, spear phishing, and malware.
4. Develop a cyber security-aware culture and create internal cyber security heroes.
5. Change behavior to eliminate the automatic trust response.
6. Make people aware of how easy it is to be tricked into providing personal and confidential information.
7. Protect your organization from data breaches and hacks.
8. Monitor employee awareness and deploy targeted anti-phishing solutions.
9. Assess the impacts of cyber security awareness training.
10. Meet industry compliance obligations.
5 Signs Of Identity Theft
Know these five signs of identity theft:
Cyber criminals know no bounds about what they will do with your stolen identity. Always verify bank, credit card, and utility statements for unusual charges and activity.
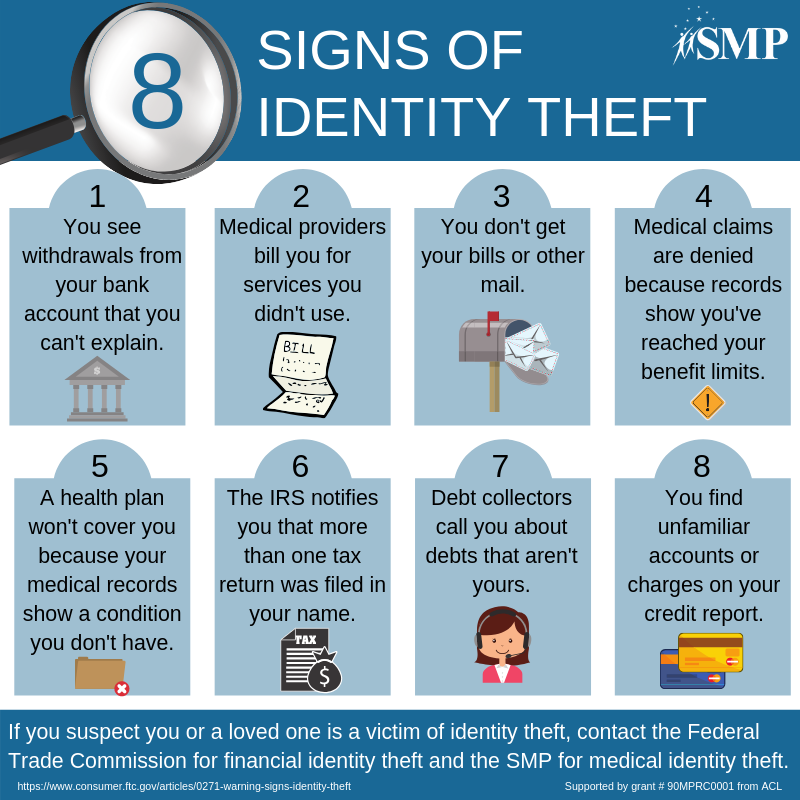
Source: SMP National Resource Center
How to Report Identity Theft
If you find yourself a victim of identity theft, number one – do not panic. Cyber criminals are looking for signs you're panicking and may contact you pretending to be an agency that can help you recover from identity theft.
Do not engage with any unauthorized providers that say they can help you resolve the issue. Instead, if you're a victim of identity theft:
- In Canada, contact the Canadian Anti-Fraud Call Centre at 1-888-495-8501.
- In the United States, contact the Federal Trade Commission at 1-877-438-4338.
- In other counties, check your government's website for information.
Learn More About Identity Theft
To learn more about identity theft and how you can keep your organization and people protected, take advantage of these free cyber security awareness resources:
Contact us at 1-866-889-5806 or at [email protected] to learn more about identity theft.
Terranova Security is committed to delivering people-centric training that makes your organization cyber security aware.


