Carrying out a cyber attack is becoming more and more accessible. For a meager price of $99, anyone can now buy a platform to steal personal data and pose a cyber threat to organizations worldwide. This accessibility is made possible through the Wi-Fi Pineapple. Learn about this new cyber threat in this article and get tips on protecting your organization.
What is a Wi-Fi Pineapple?
A Wi-Fi Pineapple is a portable device that allows cyber criminals to steal data shared on public Wi-Fi networks. For a reasonable $99, anyone can buy a Wi-Fi Pineapple and use it to steal data.
The Wi-Fi Pineapple was developed by a company that creates tools for people who work as pen testers. Organizations hire pen testers to attack their network to expose vulnerabilities so the IT team can fix these before cyber criminals discover them.
The problem is that cyber criminals have learned that they can use this device to carry out cyber attacks. The Wi-Fi Pineapple was initially designed to help defend against cyber threats but is now being used as a honeypot to commit malicious such as man-in-the-middle or spoofing attacks.
For organizations that have employees who work remotely, attend conferences, travel, or work from home, Wi-Fi Pineapple is a real threat.
Most people do not think twice about using free public Wi-Fi offered by coffee shops, airports, hotels, or the open networks provided by cities in their public parks and other open spaces.
How do Cyber Criminals use Wi-Fi Pineapple to Commit Cyber Attacks?
There are three primary ways that cyber criminals use Wi-Fi Pineapple to commit cyber attacks:
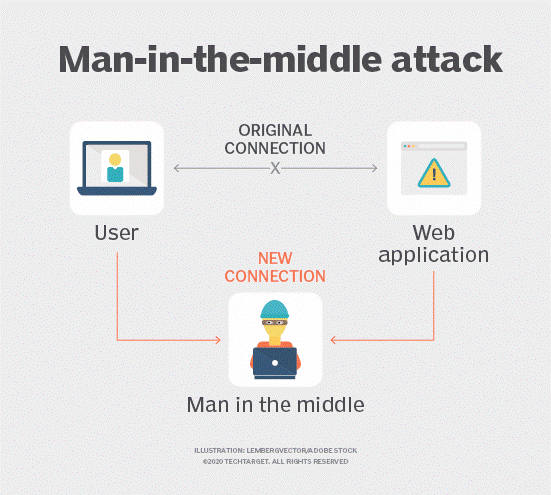
Man-In-The-Middle Attack
Source: TechTarget
The Wi-Fi Pineapple is used to eavesdrop on people using public Wi-Fi. The Pineapple is configured to act as the Wi-Fi network that people believe they are connecting to. But instead, they’re connecting to a fake network that allows cyber criminals to easily access and capture all shared data on the web.
There is no way to know if you’re connected to a legitimate public Wi-Fi or Pineapple network.
Evil Portal
To take the man-in-the-middle attack to the next level, cyber criminals create websites that look legitimate, and when people attempt to connect to the actual site, they are redirected to the faked website.
This setup makes it easy for criminals to capture login information, credit card data, and any other information you provide to the website. For example, a faked Amazon website can be used to steal credit card data, addresses, phone numbers, passwords, etc.
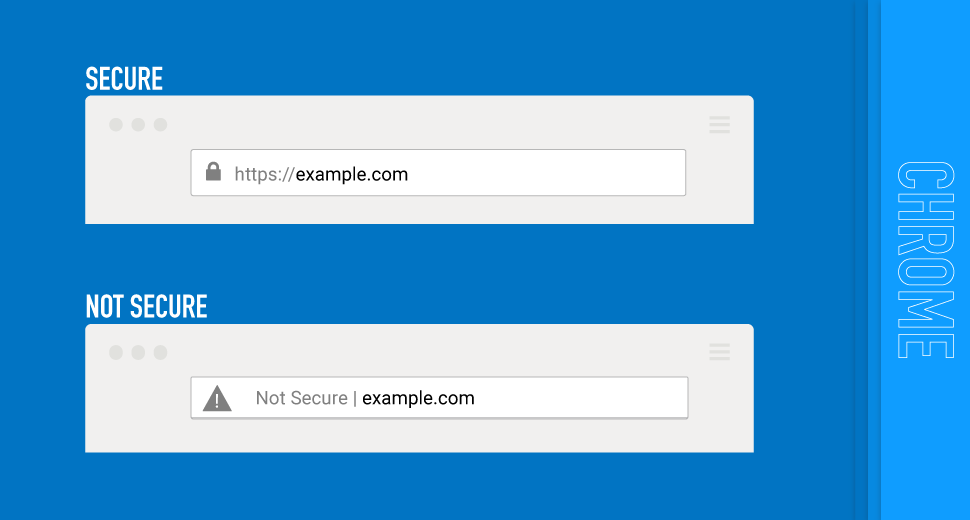
Fake HTTPS
Source: DigiCert.com
HTTPS is used to secure websites and encrypt data. This reality gives website users protection by providing a secure layer of communication. Websites that collect personal and confidential information, such as e-commerce sites, government websites, or videoconferencing, must use HTTPS.
Cyber criminals use the Wi-Fi Pineapple to direct HTTP requests (most people do not use HTTPS when typing URLs) from the real HTTPS server to their Pineapple so they can remove the secure layer protecting and encrypting data.
The only noticeable difference for the website user is the missing “lock” icon in the left corner of the URL bar.
How to Protect Your Organization from Wi-Fi Pineapple Cyber Attacks
To protect your organization from Wi-Fi Pineapple cyber attacks, remember these keys to network and corporate cyber security:
- Establish strong password rules. Enforce all employees to follow password rules requiring at least eight characters, a combination of upper- and lower-case letters, and a mixture of letters, numbers, and special characters.
- Ensure all applications, operating systems, network tools, and internal software are up-to-date and secure.
- Install malware protection and anti-spam software.
- Regularly scan for unauthorized Wi-Fi hot spots within your work perimeter.
- Always configure corporate networks that are WPA-encrypted with a password.
- For internal Wi-Fi connections, avoid SSIDs that include your organization’s name.
- Use a firewall to protect open ports from Wi-Fi Pineapple attacks, malware and ransomware attacks, and botnet attacks.
- Ensure the corporate VPN is configured to use multi-factor authentication. Only allow employees to connect to the network with a secure connection.
- Schedule regular backups of all data stored on the network and employee computers and devices.
Remember that your employees are your first line of defense against Wi-Fi Pineapple attacks.
Give your employees easy access to security awareness training that includes relevant and real-world topics, including best practices for working remotely, working from home, and traveling securely.
10 Ways to Stay Safe and Secure When You’re Away from the Office
Cyber criminals have lots of advanced and inconspicuous methods that make it easy for them to steal your personal and professional information. When working in the office, you know firewalls, VPNs, data backups, and other security measures are in place to protect you.
The threats and risks increase working remotely, attending conferences, or commuting. These ten keys to staying cyber secure when you’re away from the office can help protect you and your organization from cyber attacks:
- Never connect to open, unsecured public Wi-Fi. Even if this is the only Wi-Fi available, do not connect. Providing your email address and accepting the terms and conditions of the Wi-Fi owner does not mean you are connecting to a secure Wi-Fi.
- Only use HTTPS-protected websites. In the URL address bar, check to ensure the URL uses HTTPS and that the green lock icon is present. Never provide personal confidential information such as passwords, credit card details, or bank information on a website that does not use HTTPS.
- Turn off auto-connect. Ensure your mobile devices are not configured to automatically connect to public Wi-Fi that is not password protected.
- Configure your mobile devices and laptop to “forget” public Wi-Fi network connections. This prevents you from telling cyber criminals that you have used this public network in the past, making it difficult for them to trick you into connecting to a fake network.
- Disable Bluetooth auto-discovery. Cyber criminals listen for Bluetooth signals that they can hack to connect to mobile devices.
- Shred all documents. Do not discard personal and professional documents in garbage cans or recycling bins. If you don’t have access to a shredder, bring these documents to work and shred them in the office.
- Do not forward work emails to your personal email account. Many personal email accounts lack the security measures we use to keep our organization safe.
- Be aware of your surroundings. Do not leave your laptop open on a coffee shop table or leave your mobile device unattended at the charging station. Do not ask someone to “watch” your laptop while ordering a coffee or going to the bathroom.
Be aware of people sitting too close who may be listening to your conversations or looking at your screens.
- Always install the latest updates, patches, and versions. Ensure your computer and mobile devices have the latest applications, operating systems, network tools, and internal software installed. Ask the IT/support team to verify that your devices are up to date.
- Always connect to networks with a secure VPN. If you don’t have the VPN details, ask the IT team for this information. Consider using personal VPN software for your privacy. These options can provide some level of security if you have no other but to connect to an open Wi-Fi.
Stay vigilant. A single click can make or break your company and its reputation. For additional information on the most common cyber security risks and tips and tricks that can help you keep your sensitive data safe, visit the Cyber Security Hub.
Protecting Against Wi-Fi Pineapple Attacks with Strong Cyber Security Awareness
Your first line of defense against Wi-Fi Pineapple attacks is your employees. Ensure they are well-informed and ready to spot and prevent cyber threats before they wreak havoc on your organization. Make your employees your company’s cyber security heroes.
Cyber Security Hub: Access Exclusive Cyber Security Content
Check out our Cyber Security Hub, where you can download free, multifaceted kits on topics like working remotely, creating strong passwords, and more.