You can have the most powerful, cutting-edge security technology in the world, but if a user clicks on a malicious link in an email, allows an unauthorized person to tailgate into your building, or uses a weak password like "1234," they inadvertently expose your organization to a cybersecurity breach. The reality remains unchanged: the human risk factor is still your greatest vulnerability in cybersecurity. Human error accounts for nearly 90% of all data breach incidents, making your people the “weakest link." However, they they can also become your strongest defense.
Turn Human Risk Into Resilience
The best way to fix this situation is to create behavioral change and a culture of security across your organization. You need to find ways to encourage your users to reduce their high-risk behaviors so that security awareness becomes second nature — a mindset—and they become your “strongest link” and a key part of your cybersecurity defense strategy.
How to Achieve This?
Behavioral Change Through Continuous, Structured Efforts
Simply expecting users to follow rules or relying on sporadic 15-minute security sessions is no longer sufficient. Likewise, annual hour-long training sessions that users rush through to meet compliance requirements are ineffective in today’s fast-evolving threat landscape.
Traditional awareness training may check the compliance box, but it often fails to build true resilience. Without a long-term, adaptive strategy that keeps cybersecurity top of mind, awareness quickly fades, and vulnerabilities resurface.
Making a Human Risk Management Framework Effective
Success comes when you view security awareness as an ongoing process, not a one-time project with a clear start and end.
The most effective programs include multiple campaigns rolled out over time, each aligned with long-term strategic goals. Every campaign should have its own clear objectives, contributing to the broader mission of fostering a lasting security culture.
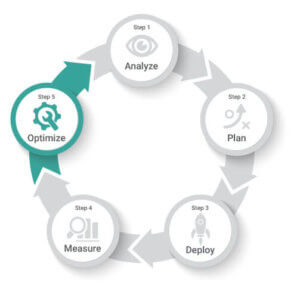
Most importantly, they follow a methodological framework built on a series of key steps:
- Step 1: Analyze
- Step 2: Plan
- Step 3: Deploy
- Step 4: Measure
- Step 5: Optimize
Without an evidence-based security awareness framework, changing risky behaviors becomes a significant challenge. A well-designed framework takes into account how people learn, adopt, and sustain new habits, ultimately fostering a culture of security awareness and greatly reducing human-related security breaches.
Step 1: Analyze
Each organization is different and yours is no exception. Everything about it is unique: your organizational culture, risk factors, staff motivation levels, compliance obligations, security awareness program maturity level and ability to deploy a program. So, when it comes to a security awareness program, it only makes sense to opt for a solution that can be personalized and adapted to the real-world needs of your organization.
What is your organization’s security awareness program maturity level? How do you determine your needs? Through analysis.
No matter how big or small your organization is, analysis is absolutely essential. It provides you with important insights, so you can create and implement a security awareness training program that addresses your current organizational culture and environment.
In your analysis, focus on nine key areas:
- Strategic program goals
- Compliance obligations of your organization
- Your different target audiences (who will receive cybersecurity training?)
- Scope (cybersecurity training topics you need to cover)
- Level of knowledge (current human risk behaviors within your organization)
- Motivation & culture (Are your people on board, indifferent or outright resistant to your program?)
- Support resources (Do you need to build a support team?)
- Globalization (Do you have to offer your program in more than one language? Will you have to customize content to reflect any geographic or cultural nuances?)
- Costs (resources and budget)
Step 2: Plan
After completing your analysis, the next step is to plan your security awareness training.
Planning takes time. However, you need to put the effort into planning if you want your security awareness training to go off without a hitch. If you simply dive into building a security awareness program hoping for the best, your outcomes will be hit and miss, and you will probably fall short of creating real behavioral change in your organization.
Planning allows you to anticipate and address roadblocks, stay aligned with your objectives and stick to your timelines and budget.
In your planning phase, you work out the logistics of your program and should focus on six specific planning essentials:
- Team (who will be on your security awareness team?)
- Roadmap (define your campaign objectives, plan your campaigns and activities for each)
- Product (i.e., select and customize online security awareness training courses, live presentations, reinforcement tools, LMS, phishing simulations, vulnerability assessments, surveys and quizzes)
- KPIs and metrics (Define KPIs and metrics in relation to each campaign’s objectives so you can measure your results against those baselines to optimize the next waves of your program.)
- Communications (i.e., communication plan, calendar, materials)
- Program presentation (to senior executives, team members or stakeholders)
Step 3: Deploy
You’ve crossed every t and dotted every i. Now you are ready to launch! Or are you?
You want your launch day to be as stress free as possible, so just before your kickoff, you should do all of your pre-testing to make sure there are no glitches. Once you’ve completed testing and any needed troubleshooting, go ahead and launch and bask in the satisfaction of a job well done.
Remember though, deployment shouldn’t end there. You want to engage people and communicate with them in interesting ways to create a buzz about your program and maximize your participation rates. You therefore need to follow up with a reinforcement phase both during and after your deployment. Doing so will help you reach the security awareness training campaign objectives you have set.
- Before you launch each campaign, test the technical functionality of your campaign, your content and the user interface.
- Launch the campaign and communicate with participants.
- Reinforce your security awareness messages using various communication tools (e.g., posters, newsletters, videos, etc.).
Step 4: Measure
Now that you have deployed your security awareness training program, you want to know how it's performing. After all, if you don’t know if it is having any impact and effectively reducing risk behaviors, you are simply going through the motions.
This is where the KPIs and metrics you identified in your planning phase come into consideration. They allow you to:
- Measure your progress according to the metrics you defined in your planning step.
- Effectively manage and monitor your campaign/program.
- Communicate information about program performance to departments across your organization and demonstrate adherence to compliance requirements.
Then you can use all of this information to evaluate performance, evaluate if you are meeting the objectives you identified in your analysis phase and move on to the final phase: optimize.
Step 5: Optimize
The purpose of applying an ongoing methodological approach — a framework — is to reduce risk behaviors over the long term. The optimization step lets you determine what works and what does not, so you can tweak your next campaign to make it even better than the previous one.
It is important to act upon your findings. Keep updating. Keep improving. That is how security awareness becomes and stays top of mind across your organization.
To optimize your program on an ongoing basis, you should:
- Analyze metrics from Step 4 – Measure
- Compare results with campaign objectives and program goals
- Identify improvement opportunities using your KIPs and metrics
- Identify new training and behavioral objectives for the next campaign.
- Conduct a postmortem meeting with your team
Need Help?
The idea of following a security awareness five-step framework may feel a little daunting, especially if you are tackling a security awareness program on your own or if you do not have access to the right resources. You may be tempted to launch a quick-fix human risk management package, or worse, take no action at all.
See how Fortra can help you break the attack chain.