Phishing has become the most common cyber threat, leading organizations to update their defenses with tools like detection systems and targeted security awareness training.
Cybercriminals are constantly evolving, finding new ways to bypass security measures. This ongoing cat-and-mouse game underscores the importance for companies to remain vigilant and adaptable.
One particularly concerning tactic on the rise is response-based scams, which blur the line between legitimate communications and phishing attempts, often evading traditional email security software.
In this article, we’ll break down response-based scams, explore why they’re so dangerous, outline effective training to help employees recognize them, and share proactive steps to stay protected — all insights drawn from Sean Bell's recent interview with ISMG.
Understanding Response-Based Scams and How They Evade Detection
Unlike traditional phishing emails that use suspicious links or attachments, response-based scams rely on plain text and social engineering tactics.
By avoiding typical red flags like hyperlinks and files, these scams can bypass many standard email security filters, making them harder to catch and easier to trust.
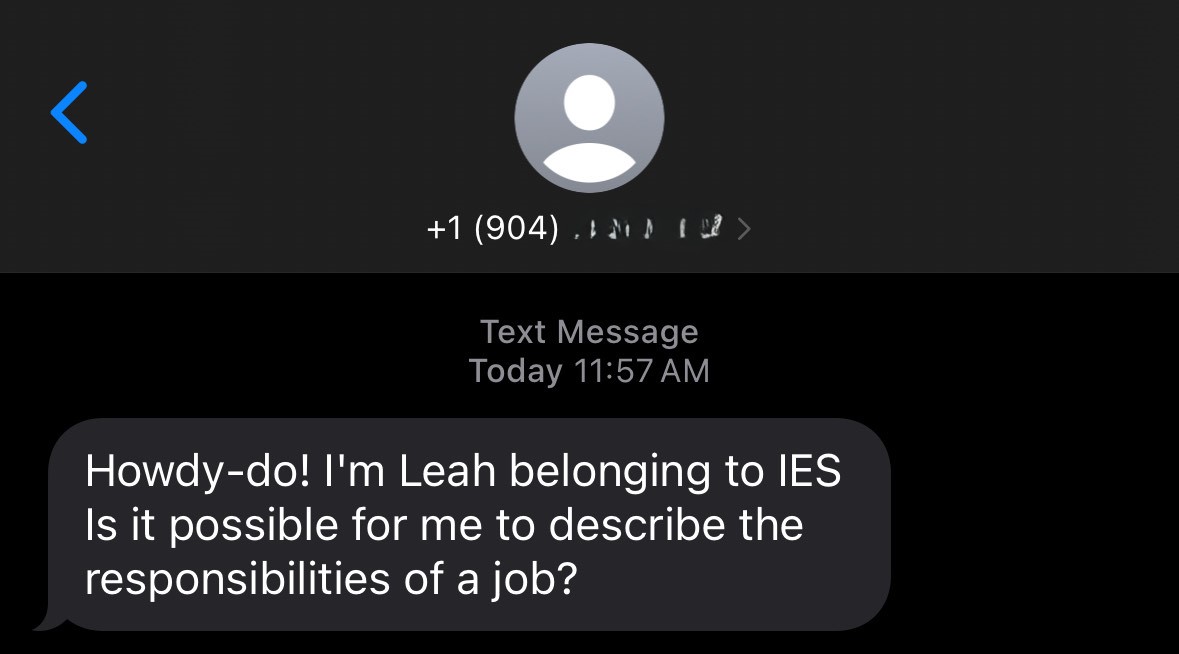
The initial communication in these attacks is benign, evading traditional security controls such as secure email gateways.
For scammers, the payoff is usually slower than traditional phishing, but it can be much larger and repeated until discovered.
The most common types of response-based scams include:
Business Email Compromise involves a scammer pretending to be someone of power within a company to gain access to funds or sensitive information. A common example could be a CEO’s email being spoofed to approve wire transfers.
Job scams start through emails or fake ads on job sites. Candidates are offered the job on the spot but asked to send money to pay for training or to cash a check and send money back, at which point the scammers disappear.
Tech support scams happen when scammers pretend to be someone’s coworkers in tech support and ask for remote access to fix an issue. Once this access is granted, the scammers steal sensitive information from the device.
Advanced fee fraud involves requesting upfront payments to unlock rewards, like an inheritance or investment opportunity. It can also target companies by sending fake invoices to accounts payable departments, seeking payment to start fictitious work.
This type of cyber-attack heavily relies on mistakes amplified by global working environments and the advent of generative AI tools like ChatGPT, which reduces the barrier to entry and increases their success by creating convincing messages at scale.
The Human Element: Why Employee Awareness Is Crucial
To combat this threat efficiently, your users have to be knowledgeable in spotting and reporting red flags that your security operation systems might have missed.
Here are the most common tactics used by cybercriminals in this type of attack that employees must be vigilant about:
A sense of urgency in requesting information or paying an invoice on a tight timeline makes the victim feel pressured to skip their routine security checks.
Moving conversations outside of monitored channels such as text messages or a social media platform to further evade company measures against these cyber-attacks.
Building trust over time, often starting from a very innocuous message or wrong number text messages so that the victim never suspects they are being scammed.
If users are made aware of these schemes and receive training to detect them before it’s too late, response-based scams lose much of their potency.
Proactive Steps Organizations Can Take to Detect and Prevent Scams
Staying protected against response-based scams requires a layered security strategy.
Email security tools
While some scam emails get through email security solutions, having them in place is still a good idea. Certain domain names will still get flagged before they reach a user or might trigger a notification that the user has never interacted with this address.
Additionally, some tools integrate AI detection software to filter out emails created this way, dramatically reducing the amount of these cyber-attacks before they reach inboxes. These solutions also allow you to monitor any suspicious activity.
Cybersecurity awareness is key
Since these threats exclusively target employees, your users must be well-trained to recognize these attacks. All departments should be trained regularly on the up-and-coming trends for this type of crime.
Simulations are especially useful in combatting response-based scams by providing the appropriate context to users after they’ve received training. This measure will allow you to assess knowledge levels and identify which stages of the scam your staff needs to work on to remain protected.
Incident response plans for response-based scams
As with any other cyber-attack, a detailed incident response plan can help minimize the impact of a security breach.
Emphasize the importance of reporting fraudulent emails as soon as they are received and foster an environment where your users aren’t scared to alert you when they accidentally click on a malicious email.
Since these attacks usually burn longer than the typical phishing attack, catching them early can potentially completely negate the attempt, and their effects could be heavily mitigated if they are reported immediately.
Stay One Step Ahead of Response-Based Scams
Training employees to recognize and respond to suspicious activities is vital. Still, it must be part of a layered approach that includes regular threat assessments, updated incident response protocols, and continuous adaptation to evolving scam techniques.
Evaluate the effectiveness of your training initiatives, update response plans based on the latest threat intelligence, and consider incorporating simulations or phishing drills to reinforce learning.
Check out Sean Bell's full interview for more real-world examples and insights on the other ways cybercriminals manipulate their targets.