- An urgent voicemail message from the tax department.
- A text message from Microsoft tech support warning you about a problem with your computer.
- A caller asking you to confirm your mailing address and credit card number so you can collect your free prize.
- A text message requesting your confirmation of an Amazon shipment.
These are all examples of smishing and vishing cyber attacks. They have one thing in common: they happen over the phone.
Phones are now an essential part of our daily lives. This is also why it has become one of the most popular contact methods for cyber criminals. Both smishing and vishing rely on social engineering to trick victims into giving up personal and confidential information.
Both use persuasive and often urgent language to manipulate victims into giving up information such as their bank account details, passwords, social insurance number, and mailing address.
But how are smishing and vishing different from each other? Here's how to identify each type of scam.
What is Smishing?
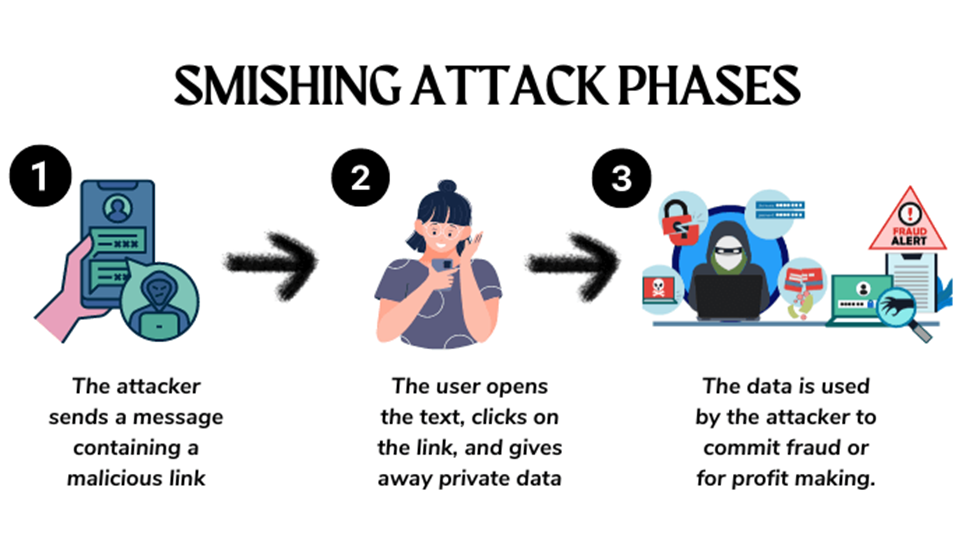
Source: Heimdal Security
Smishing is a cyber crime that uses manipulative text messages to steal confidential personal and corporate information from people.
Using urgent and compelling language, the text message may threaten the victim with severe consequences if they don't take action or convince the victim that they're helping the sender by providing the requested information.
Cyber criminals take advantage of text messages because they know how frequently people check their phones. Consider these recent SMS marketing statistics:
- SMS has a 98% open rate, significantly higher than email marketing (20%).
- 60% of people open and read text messages within 1-5 minutes of receiving them.
- 80% of consumers recoup discounts and coupons using their mobile devices.
- Users are 4.5 times more likely to respond to a text than an email.
To make things easier for cyber criminals, people are unaware of smishing cyber attacks. This lack of awareness creates a dangerous scenario where victims do not think twice about tapping embedded links, providing information, or responding to the texting cyber criminal.
What is Vishing?
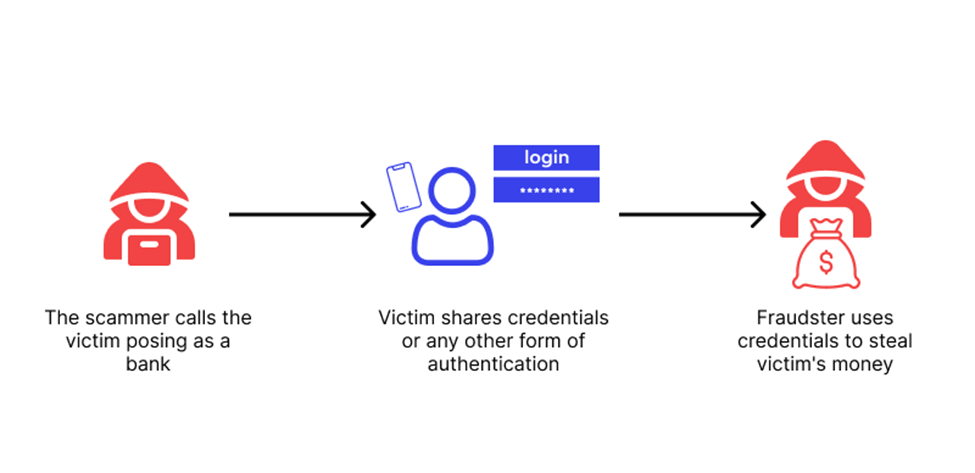
Source: Wallarm
Vishing happens over a phone call, but the goal is the same: to steal personal information from victims. Often called voice phishing, cyber criminals use savvy social engineering tactics to convince victims to give up private information before they can even think.
Cyber criminals often tailor their vishing calls and messages to the time of the year or a hot news story. For example, during tax season, criminals leave messages pretending to be from the IRS.
To execute this scam, a cyber criminal may research a company on different platforms like LinkedIn or the company website to collect details about the leadership, employees, and who is traveling or attending a conference.
With this information, the cyber criminal makes strategic phone calls and voicemails that convince other employees to transfer funds on behalf of their manager, who is traveling and cannot access the network.
What is the Difference Between Smishing and Vishing
Both smishing and vishing are carried out by cyber criminals to steal personal information from the victim. These can include their credit card numbers and bank details. However, these two approaches differ in how they are carried out.
Smishing is done via text or instant messaging apps like WhatsApp and Telegram. The scammer provides their victim with a link, which, when clicked, will help them steal personal information or upload malware.
Vishing, on the other hand, uses phone calls and voicemail to reach the victim. They will pretend to be representatives of a bank or other institution to retrieve personal information. AI has also made vishing more possible, with AI tools used to mimic a person's voice and trick the victim into sending them money or sharing data.
6 Ways You Can Recognize Smishing and Vishing Attacks
We know it can be hard to stay current with the latest cyber attack methods and threats. This is why we want you to be able to recognize smishing and vishing attacks.
Cyber criminals use convincing text messages, voicemails, and phone calls to trick people into providing personal and professional confidential information. Like phishing, this information is then used to steal and harm.
When you receive a text message, voicemail, or phone call from someone you do not know, please remember these six tips to recognize and prevent smishing and vishing attacks:
- You don't know the caller or the sender. If you're not expecting a call or a text, don't respond or pick up the call. Do not tap any embedded attachments, URLs, or images.
- They claim to be from an official source. Remember that the tax department, local hospital, police, or bank will never call and leave a threatening voicemail demanding you act or face criminal prosecution. If you are concerned, use the official website of the organization to find their contact information and send an email about the voicemail or phone call.
- They are using urgent language. Be on the lookout for text messages and phone calls that use convincing, forceful, or urgent language. Cyber criminals try to prey on the basic human instincts of trust, fear, greed, and wanting to help to convince people to provide personal information.
- They are asking for sensitive information. Never give out bank account details, personnel files, or password details. No legitimate company or co-worker will ask for these from you over the phone, via text message, or social media.
- The offer is too good to be true. Winning a prize can be exciting, which is precisely why cyber criminals use this tactic. Remember to stop and think before you give out any information. If it's good to be true, it probably is.
Always think before you click. Read the text message carefully. Listen to the caller or voicemail critically. Pay attention to signs of social engineering.
Remember that fear is a common tactic with smishing and vishing—the cyber criminal attempts to scare you into acting. Be aware of threats about criminal prosecution, jail time, freezing of accounts, or loss of healthcare benefits.
How To Protect Your Organization and Employees from Smishing and Vishing Attacks
It's easy to overlook the threat risk of smishing and vishing since there is a high focus on phishing, spear phishing, malware, and CEO fraud. However, smishing and vishing attacks are common vectors for cyber criminals who target organizations and their employees.
These statistics on smishing and vishing from a global 2023 survey of organization security leaders and employees reveal how important it is to raise awareness of these cyber threats:
- 49% of employees answered I Don't Know to the question: What is Smishing?
- 53% of employees answered I Don't Know to the question: What is Vishing?
- 84% of surveyed CISOs and security leaders received corporate smishing attacks.
- 83% of surveyed CISOs and security leaders received corporate vishing attacks.
To protect your organization and employees from smishing and vishing attacks, do the following:
- Take advantage of security awareness training that uses real-world examples of smishing and vishing attacks to reinforce how cyber criminals use text messaging and phone calls to commit cyber fraud.
- Make it easy for employees to report smishing and vishing attacks to you and your team.
- If you have a BYOD policy, it's essential to have strict rules around app updates, password protection, Wi-Fi connectivity and follow recommended remote and mobile device cyber security best practices.
- Use phishing simulations to measure and monitor employee awareness of cyber fraud threats. Use this information to customize your security awareness training and campaign to address areas where your employees need additional education.
Remember, your employees are your first defense against smishing and vishing attacks. Focus on giving your employees relatable, modern, and relevant security awareness training. When employees understand how smishing and vishing happen and the ramifications of a successful smish or vish attack, they are more likely to be alert to threats.
![]()
Protect Yourself From Smishing and Vishing Attacks
Protecting your company from smishing or vishing attacks starts with training your employees. Make them cyber heroes who can spot threats, strengthen data protection, and protect your organization by downloading Terranova Security's Cyber Security Hub.


