Security Awareness Training
Enhance your training program with fun, engaging security awareness content that supports cyber security leaders and their behavior change initiatives. Enjoy multilingual, mobile responsive, and accessible content that makes security awareness training available to all users and promotes an inclusive atmosphere.
Quizzes
Test end user knowledge retention from your security awareness courses with quizzes that utilize different question formats. Pull from a bank of pre-configured quiz questions or create your own to ensure your users are receiving the most pertinent testing material and response feedback possible.
Secure Sensitive Information and Reduce Risk
Strengthen your information security and build key cyber threat resilience with powerful, easy-to-use security awareness training and phishing simulations. With a wide range of content that leverages over 20 years of cyber security expertise, Terranova Security delivers a powerful learning experience that supports your cyber security goals and changes user behavior.
Engaging Security Awareness Training
Get the highest-quality security awareness training content in the industry with customizable, immersive courses, quizzes, and modules. Everything you need to train your cyber heroes is at your fingertips.
Real-World Phishing Simulations
Test and deepen cyber threat knowledge with customizable phishing simulations that reflect current real-world attacks. Give your end users the opportunity to safely test their skills and ensure everyone can consistently detect and report phishing, social engineering, and other types of threats.
An Easy-To-Use, Intuitive Platform
Manage every aspect of your security awareness training and phishing simulation campaigns with ease on the Terranova Security Awareness Platform. Deploy courses, send email updates and reminders, track end user performance, and edit your campaign content – all in just a few clicks.
Key Features of the Security Awareness Platform
Build Your Security Awareness Training Bundle
| Classic | Selection | Ultimate | |
|---|---|---|---|
|
Languages |
3 | 3 | All Available |
|
General Knowledge End User Library (courses available in mobile responsive or WCAG 2.0 accessible versions) Cyber Game Risk-Based
Role-Based Compliance & Privacy |
Select 18 Training Assets | Select 36 Training Assets | Complete Library |
|
Communication & Reinforcement Tools
|
18 | 36 | Complete Library |
| Total Number of Training Assets | 36 | 72 | Unlimited* 1000+ |
|
Security Awareness Platform
|
• | • | • |
|
Security Awareness Resources
|
• | • |
Security Awareness Library
General Knowledge
End User
- Access Control
- Bring Your Own Device (BYOD)
- Business Email Compromise
- Cloud Services
- Confidentiality on the Web
- Data Leakage
- Identity Theft
- Incident Reporting
- Information Classification
- Information Lifecycle
- Intellectual Property
- Introduction to Information Security
- Malware
- Mobile Devices
- Open Wi-Fi Risks
- Password
- Phishing
- Phishing Websites
- Physical Security
- Privacy
- Protecting Payment Card Data
- Protecting Your Home Computer
- Ransomware
- Responsible Use of the Internet
- Smartphones
- Social Engineering
- Social Networks
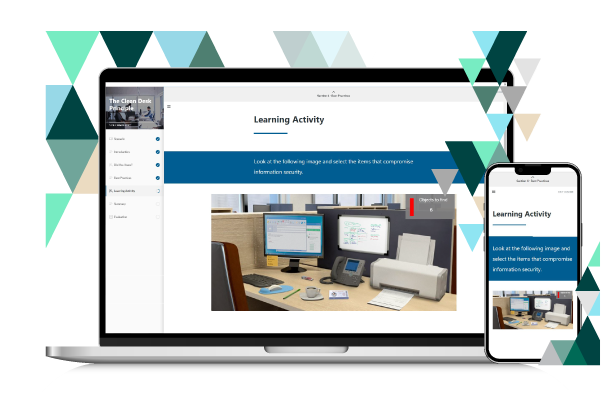
- The Clean Desk Principle
- Traveling Securely
- Unintentional Insider Threat
- Working Remotely
3D Cartoon Characters

Real Action Characters

Cyber Game
Serious Game
- BEC
- Cloud Based Services
- Data Transfer
- Ransomware
- Securing the Home Office
- Social Engineering
- Social Networks
- Strong Password
Cyber Challenge
- Cloud Services
- Incident Identification for Reporting
- Information Classification
- Information Lifecycle
- Malware
- Mobile Devices
- Phishing
- Privacy
- Protecting Your Home Office
- Ransomware
- Social Engineering
- Traveling Securely
Risk-Based
Microlearnings
- Access Control
- Applying the Clean Desk Principle
- Authentication method
- Business Email Compromised (BEC)
- C-Level Email Impersonation
- Cyber Quiz
- Friend or Foe?
- Handling Unidentifed Indivduals
- Mass Market Phishing
- OAuth consent grant
- Phishing by Phone
- Policy Tips Around Sensitive Information
- Ransomware
- Report Message
- Risky USB
- Securing the Home Office Environment
- Sharing an Organization Computer
- Smishing
- Spear Phishing
- Teams phishing
- Understanding App Consent Requests
- Unintentional Insider Threat
- Unsecured Sharing of Sensitive Documents
- Vishing
- Web Phishing
- Whaling
Nanolearnings
- Anatomy of a Spear Phishing Attack
- Being Security Aware
- Cloud-Based Sharing
- Credential Theft
- Cyber Attack Detection
- Identity Theft - Example of an Attack
- Double Barrel Phishing Attack
- Insider Threat
- Phishing - Six Clues That Should Raise Your Suspicions
- Phishing Website
- Preventing Security Breaches
- Protecting Sensitive Information - Information Handling
- Ransomware
- Smishing
- Social Engineering
- Social Engineering via Email
- Social Networks
- Spear Phishing - The CEO Fraud
- Spoofing
- Stegosploit
- Vishing
- Web Conferences Risks
- Wi-Fi Security
- What is two-factor authentication
Nanovideos
- Credential Theft
- Cyber Fraud
- Employee Data Breach
- Financial Data Exposure
- Identity Theft
- Importance of Security Culture in the Organization
- Malicious Software
- Ransomware
- Website URL
Role-based
Information Security Awareness for:
- Executives
- Introduction to Information Security
- Passwords
- Phishing
- Confidentiality on the Web
- Mobile Devices
- Data Leakage
- Business Email Compromise
- Finance
- Introduction to Information Security
- Passwords
- Phishing
- Confidentiality on the Web
- Protecting Payment Card Data
- Data Leakage
- Help Desk
- Introduction to Information Security
- Passwords
- Access Control
- Social Engineering
- Phishing
- Incident Reporting
- Human Resources
- Introduction to Information Security
- Passwords
- Phishing
- Confidentiality on the Web
- Privacy
- Data Leakage
- IT Administrators
- Network Security Overview
- Common Network Attacks
- Securing Networks
- Securing Data Repositories
- IT Developers
- Application Security Overview
- Common Application Attacks
- Secure Development
- Cryptography Overview
- Access Control
- Information Lifecycle
- IT Privileged Users
- Introduction to Information Security
- Passwords
- Access Control
- Phishing
- Malware
- Ransomware
- Unintentional Insider Threat
- Incident Reporting
- Working Remotely
- Managers
- Security Challenges
- Security Governance
- Leading by Example
- OWASP
- Open Web Application Security Project (OWASP)
Compliance & Privacy
- CCPA Essentials
- GDPR Essentials
- GDPR for Procurement Employees
- HIPAA/HITECH
- Personal information protection in the private sector in Quebec
- Key aspects of the reform
- Companies’ obligations
- Default protection of personal information
- Individuals’ rights, and how to protect their information
- Personally Identifiable Information (PII)
- PCI DSS Awareness
- PCI DSS Awareness
- PCI DSS for Retailers
- PCI DSS for Call Centers
- POPI Act
- Privacy Essentials
- The Protection of Personal Data
- Collecting Personal Data
- Privacy Principles
- Privacy Breaches
- Protected Health Information (PHI)
- Protected Health Information for Europe
- Security by Design (SBD)
Communication & Reinforcement Tools
Increase employee engagement with a diverse suite of communication tools, with new assets added regularly
- Newsletters: Send training updates and security best practice highlights directly to your users.
- Posters: Promote your training program with visuals you can tailor to match your brand.
- Wallpapers and Web Banners: Increase program engagement with vivid, thought-provoking digital messaging.
- Comics: Add a fun visual aspect to your training program with short comics depicting characters in relatable scenarios.
- Infographics: Share cyber security tips and best practices in a compact, engaging format that’s perfect for social or intranets.
- Cyberpedia: Get everything you need to know about key cyber security topics in exhaustive, informative webpages.
- What is Videos: Send cyber security tips and best practices to users in bite-sized streaming video format.
All communication tools are currently available in EN, FR-CA, FR-FR, and ES LATAM. For additional language support, please contact the Terranova Security Customer Success team.
Industry-Leading Security Awareness Training Solutions
Maximize your security awareness investment and safeguard all your organization’s important digital assets with inclusive phishing training that’s flexible and powerful. With interactive modules available in a variety of different content formats, you can provide users with an immersive training experience.
Accessibility Compliance

Make security awareness training available to all end users with WCAG compliant training content.
Mobile Responsive Training

Give users the flexibility they need to complete training modules on their preferred device.
Gamification
Boost participation and encourage training course completion with interactive gamification elements.
Different Training Formats

Utilize a variety of content formats like microlearning and nanolearning, as well as nanovideos and serious games, to reinforce key concepts.
A Diverse, Inclusive Training Approach

Deliver training to a global user base with security awareness content available in over 40 languages.
Security Awareness Training Languages
Training cyber heroes is a worldwide movement, which makes language a crucial component. Empower your employees by offering security awareness training in their preferred language.
- EN English
- EN-GB English (United Kingdom)
- FR French (Canada)
- FR-FR French (France)
- ES Spanish (Latin America)
- ES-ES Spanish (Spain)
- AR Arabic
- CS Czech
- DA Danish
- DE German
- EL Greek
- FA Persian
- FI Finnish
- HE Hebrew
- HI Hindi
- HR Croatian
- HU Hungarian
- ID Indonesian
- IT Italian
- JA Japanese
- KO Korean
- MS-MY Malay (Malaysia)
- NB Norwegian
- NL Dutch
- PL Polish
- PT Portuguese (Brazil)
- PT-PT Portuguese (Portugal)
- RO Romanian
- RU Russian
- SK Slovak
- SR Serbian
- SV Swedish
- TH Thai
- TR Turkish
- UK Ukrainian
- VI Vietnamese
- ZH-HK Chinese (Hong Kong) (script traditional; narration cantonese)
- ZH-CN Chinese (PRC*) (script simplified; narration mandarin)
- ZH-TW Chinese (Taiwan) (script traditional; narration mandarin)
Terranova Security and Microsoft:
Bringing the Best Security Awareness Content to Users
Terranova Security is Microsoft’s security awareness training partner of choice, helping organizations worldwide leverage high-quality content to strengthen their data protection. Terranova Security training material also leverages Microsoft’s real-time phishing intel to reflect the most current cyber threats and help users safeguard all types of information.
Industry Distinctions
Recognized by Gartner as a representative vendor in the 2021 Market Guide for:
Security Awareness Computer-Based Training

Customer excellence is a driving force and core value across the entire Terranova Security team.
This distinction is validation by our customers that we are making a difference and supporting them in their security awareness training journey.

2021 Security Awareness & Training Data Quadrant Report
Gold Medal Winner - Security Awareness Training
Engaging, Informative Content for All Users
Get access to fun, instantly shareable educational information security content on Terranova Security’s new free resource: The Cyber Security Hub!
Topics covered on the Hub include (but are not limited to) Phishing, Social Engineering, Working from Home and Strong Passwords.