Many organizations face regulatory requirements to train employees on cybersecurity threats, but simply meeting these standards doesn't mean you’re protecting your people and your data. Effective training goes beyond compliance, offering frequent exposure to new ideas, regular repetition, practical application, and continuous assessment. This is where targeted training types come into play.
Targeted training types allow organizations to tailor content to their unique needs and goals. Formats like end-user training, role-based modules, and phishing simulations boost engagement, address emerging threats, and strengthen knowledge retention. A strategic blend of these formats helps build a flexible, scalable training program that effectively meets their unique challenges.
In this article, we explore different training types in a cybersecurity program, detailing their uses and goals to help you build the most effective program for your users.
Understanding the Training Types
Each piece of training within a learning program has a specific purpose. The following segments can all work together to start or update your program.
End-User Training
| Best for | When to use it |
| New employees, employees who need a refresher course, introducing cybersecurity awareness concepts | Onboarding new employees, general refresher, as part of your annual program |
End-user training consists of 32 modules that serve as the foundation for any cybersecurity awareness program. Its goal is to provide a strong base so users understand the most common cyber threats, reducing the risks tied to the human element of your business. It covers many threats to increase general awareness in your company, making it ideal for onboarding new employees and as a yearly refresher for all.
Role-Based Training
| Best for | When to use it |
| Employees who handle sensitive information, specific departments with unique cybersecurity needs | During onboarding, for specialized departmental training, and for regular updates to reflect the latest threats |
Role-based training provides personalized content for specific groups. Different departments have unique cybersecurity training needs. For example:
- Finance: Protecting payment card data, data leakage
- Human Resources: Privacy, confidentiality on the web
- IT Administrators: Securing networks, common network attacks
Role-based training resonates with employees' daily responsibilities and the unique threats they face, making it more likely they will retain information and apply it to their workflows.
Real-World Phishing Simulations
| Best for | When to use it |
| All employees, especially those who frequently handle sensitive information | Regularly, to continually assess and improve employees' ability to recognize phishing attempts. After training sessions to gauge effectiveness. When introducing new employees to cybersecurity practices |
Phishing simulations test employees against recent phishing threats by sending targeted emails to assess their ability to recognize phishing attempts. This helps staff practice recognizing phishing signals in a safe environment.
Risk-Based Training
| Best for | When to use it |
| Employees in high-risk roles, such as IT staff, financial departments, executives, and customer service representatives | When your IT department identifies specific, high-risk threats like vishing or spoofing |
Risk-based training addresses specific threats identified by your IT department, ensuring the organization focuses on the most dangerous and frequent risks. It includes microlearning, nanolearning, and nanovideos, which are designed to address specific threats and keep training relevant and engaging.
Micro and NanoLearning
| Best for | When to use it |
| Teams with limited training time, employees who prefer brief, engaging content, and roles needing quick, actionable insights | When introducing new cyber threats or updates, to reinforce previous training with quick refreshers |
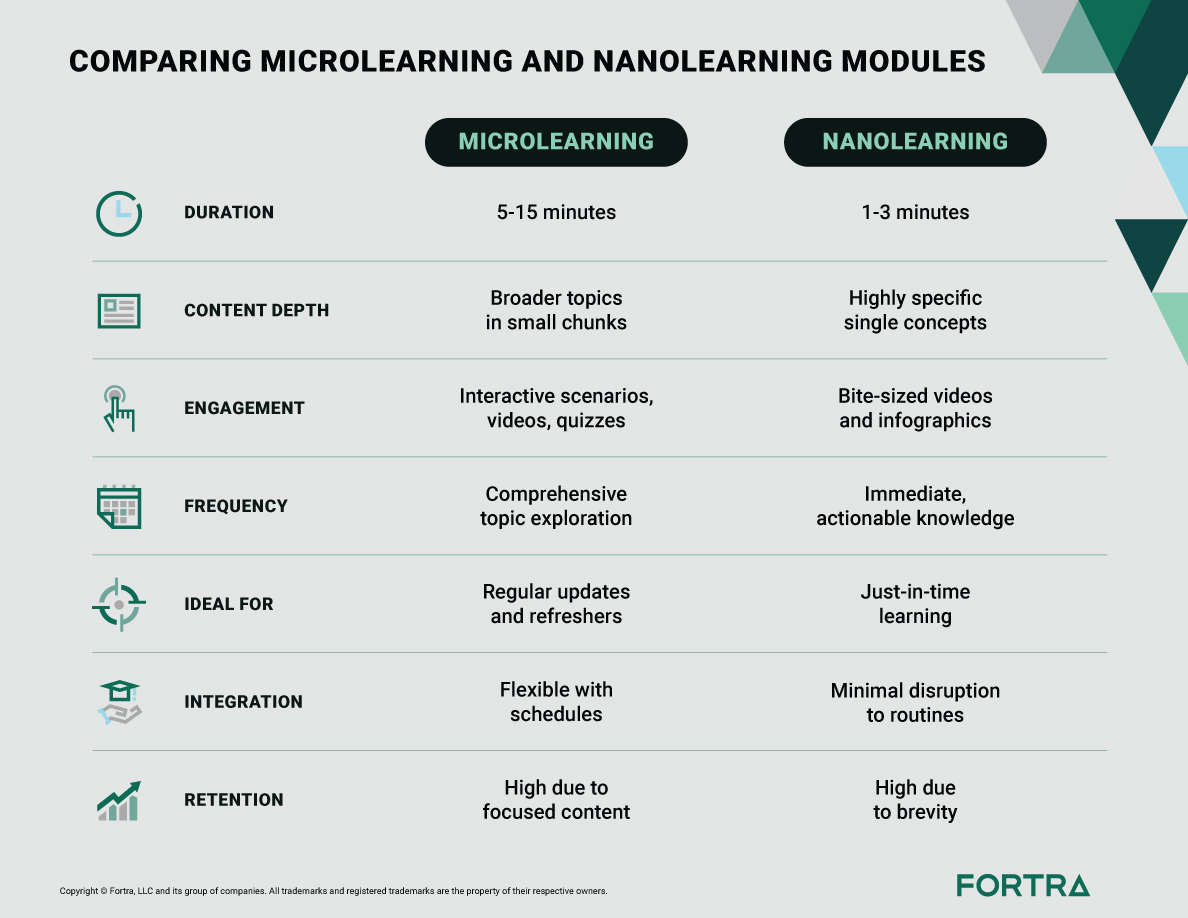
Microlearning involves scenario-based teachings and quizzes lasting 5 to 15 minutes, providing a brief overview of a cyber threat. Nanolearning takes under 5 minutes to complete, perfect for just-in-time training and targeting a specific aspect of a cybersecurity topic. These short, focused sessions are ideal for rapidly evolving threats.
Comparison
Nanovideo
| Best for | When to use it |
| Employees who prefer visual content, roles needing quick, clear demonstrations, and teams with limited training time | When introducing new subjects or risks, for putting topics into context, and as intermissions in longer training sessions |
Nanovideos are particularly effective because they capture attention, clearly demonstrate concepts, and enhance retention. They are great for introducing new subjects or risks, putting them into context, and reinforcing key topics. They can be used in sporadic training or as intermissions between sections of a longer training program to maintain engagement and retention.
Cyber Games
| Best for | When to use it |
| Organizations aiming to boost participation and completion rates, all employees, especially those who find traditional training methods tedious | When traditional training methods fail to engage employees, during cybersecurity awareness campaigns, or when focusing on high-risk behaviors |
Cyber Games are interactive modules that reinforce cybersecurity best practices through gamification. They increase motivation, enhance participation, reinforce learning, and build healthy competition.
Types of cyber games include:
- Cyber Challenge, which uses leaderboards to track awareness training, and
- Serious Games, which immerse employees in scenarios to test their knowledge.
Compliance and Privacy Training
| Best for | When to use it |
| Employees in regulated industries (healthcare, finance, legal) and roles handling sensitive information | During onboarding, with regulatory updates (e.g., HIPAA, GDPR), and regularly to reinforce standards |
Compliance and privacy training is essential for meeting legal requirements and staying updated with regulations. It ensures employees understand and adhere to compliance and privacy standards, protecting sensitive information and maintaining regulatory compliance.
An Example: Changing User Behavior About Opening Malicious Links
To illustrate how these targeted training types can work together, consider the goal of changing users' behavior about phishing. Here's how you can leverage different training types to achieve this:
- End-User Training: Start with a broad module on recognizing phishing attempts, covering basic concepts and common tactics used by attackers.
- Microlearning: Follow up with a short, focused session on specific phishing tactics, such as identifying suspicious emails and links.
- Nanolearning: Provide quick, targeted lessons on the latest phishing threats and how to respond, taking under five minutes to complete.
- Phishing Simulation: Conduct regular phishing simulations to test employees' ability to apply what they've learned in recognizing and avoiding phishing attempts.
- Cyber Games: Introduce a cyber challenge game that rewards employees for correctly identifying phishing attempts, fostering a competitive yet educational environment.
By integrating these training types, you create a comprehensive and engaging learning experience that reinforces good cybersecurity practices and reduces the risk of users opening malicious links.
For employees who struggle with these concepts, consider implementing remedial training to reinforce learning and ensure everyone is up to speed.
Targeted training types enhance cybersecurity awareness by providing frequent, timely sessions that keep employees updated and informed.
Explore our Security Awareness Training Kit to guide you through each step of implementing the different training types throughout your program.
The Power of Targeted Training Types in Cybersecurity Education
Proactiveness is key in modern cybersecurity. Threats change daily, and the best way to keep your employees updated is with frequent, timely training sessions to ensure they have the freshest information.
Targeted training formats allow you to combine different teaching methods to improve knowledge retention in your most important training areas.
Explore how these targeted training formats can enhance your cybersecurity awareness program. Preview our training videos here.
