Retail stores are one of the oldest ways humans exchange goods and services. As they evolve, one of the most significant shifts they have undergone is the dramatic increase in technology integration within their operations.
From tools to check stock to staffing management and cash registers, retail stores rely heavily on technology for almost every aspect of their business. Unfortunately, all these improvements come with challenges
With the vast amount of transactions and customer data they hold, it’s no wonder how they’ve become prime targets for cyber attacks.
Retail is the third most targeted industry for cyber attacks. Not only do that, but they also see the whole gamut and experience a wide variety of cyber threats.
This article will explain why this sector sees increased cyber threat activity, analyze its different attack vectors, and provide tips for retail stores to protect themselves better.
The Retail Sector Today
Today, the retail sector is among the industries rapidly sprinting towards modern technologies and digital solutions.
In the last three years, it has experienced a decade’s worth of growth and is expected to keep growing at a moderate pace. While this is a good effort toward the sector’s development, it’s also posing a risk to cyber security.
As technologies develop, so do the strategies attackers employ to gain access to data. With the retail industry entrusted with sensitive data like credit card details, addresses, financial records, and purchase histories, it’s becoming a prime target for cyber attacks, with 77% of retail organizations facing an attack in 2022.
The Cyber Threats and the Retail Industry
With the retail industry experiencing a 57% increase in cyber threats in the last two years, it’s fair to say that companies in this industry need a robust cyber security plan to keep sensitive user and payment data safe.
Data breaches seem to be the most common end goal for retail cyber attacks, leading the industry to have the third highest rate of data breaches in 2022 behind healthcare and education.
While most attacks end up only exposing basic personal identifiers like names and other personal information, the situation can quickly deteriorate if the victim has poor password hygiene.
Severe attacks where payment information is exposed are on the rise. Hackers broke the defenses of Target in 2013, exposing 41 million payment cards and the personal information of 70 million customers.
Home Depot was hit with malware affecting 52 million customers’ payment information in 2014, and an attacker managed to steal the credit card information of 4.6 million Neiman Marcus customers in 2021.
In 2023, retailer JD Sports dealt with a cyber attack where cyber criminals gained access to their database of purchases between 2018 and 2020, retrieving customer data such as their full name, delivery and billing addresses, phone numbers, email addresses, order details, and the last four digits of their cards.
Why is retail a prime target for cyber attacks?
With so many high-profile cyber attacks against retail stores, it’s important to know why hackers seem to prefer them. Retail stores across all industries often have the perfect storm of large amounts of recorded payment information, a varied third-party vendor roster, and a high turnover rate.
This means retail stores have extremely valuable information stored on an incredibly difficult-to-secure system. The high turnover can be especially dangerous since it leads to improper cyber security awareness training, making retailers vulnerable to phishing attacks.
These attacks are especially prevalent during peak online shopping seasons, including Black Friday and Cyber Monday. Black Friday scams, particularly phishing, are on the rise, with over 351,000 emails containing the term “Black Friday” during the shopping season.
At a time when most shoppers are rushing to make purchases online, cyber attackers are also deploying Black Friday express delivery and gift card scam strategies, among others, to take advantage of the rush.
How Cyber Criminals Target Retail
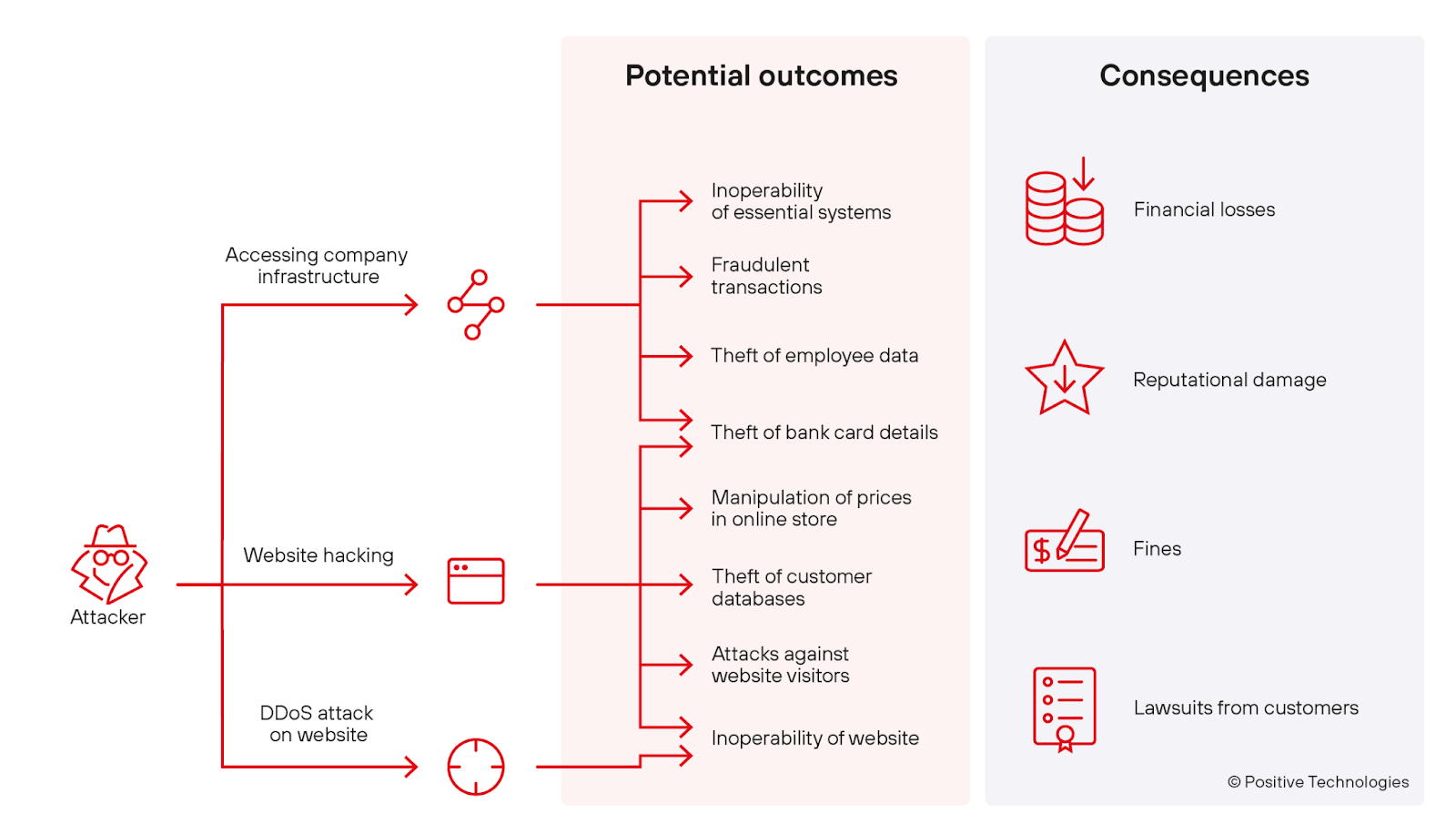
Source: Positive Technologies
While some industries, like healthcare, see mostly ransomware attacks, the retail sector has to stay on its toes at all times and on all fronts. Since retailers use a myriad of hardware and software technology, the number of vulnerabilities ends up being very high within these organizations.
Phishing
Phishing attacks can be particularly successful against retail stores because some workers often don’t have dedicated work emails and don’t use them in their day-to-day activities. These emails are often used in transactions, even when workers are unfamiliar with essential phishing detection.
From ordering stock to dealing with logistic partners, links leading to external sites are the norm for retail stores. Hackers have become masters of disguise and can easily fool a distracted worker with spear phishing tactics.
Malware
The Home Depot attack happened precisely because their POS system was infected with a malware program designed to steal credit card information as transactions were processed. The breach took several months to be noticed and affected millions of customers.
Retail store devices such as cash registers and POS systems have undergone significant evolution to the point of becoming mini-computers running semi-traditional operating systems that can be easily infected.
Additionally, the increased internet connectivity of these devices makes them an easier target for hackers.
Ransomware
These are the types of attacks retailers see the least, but they can still be crippling to a large network of stores. Larger retailers often keep stores in the same country or district on one payment or cash register system to simplify their processes.
This means a ransomware attack can prevent a retailer from taking card payments or recording transactions if it affects the cash register system. Cyber criminals can then rely on the urgency of the situation to get the victim to pay them to resume their operations.
Third-Party Risk Management for Retailers
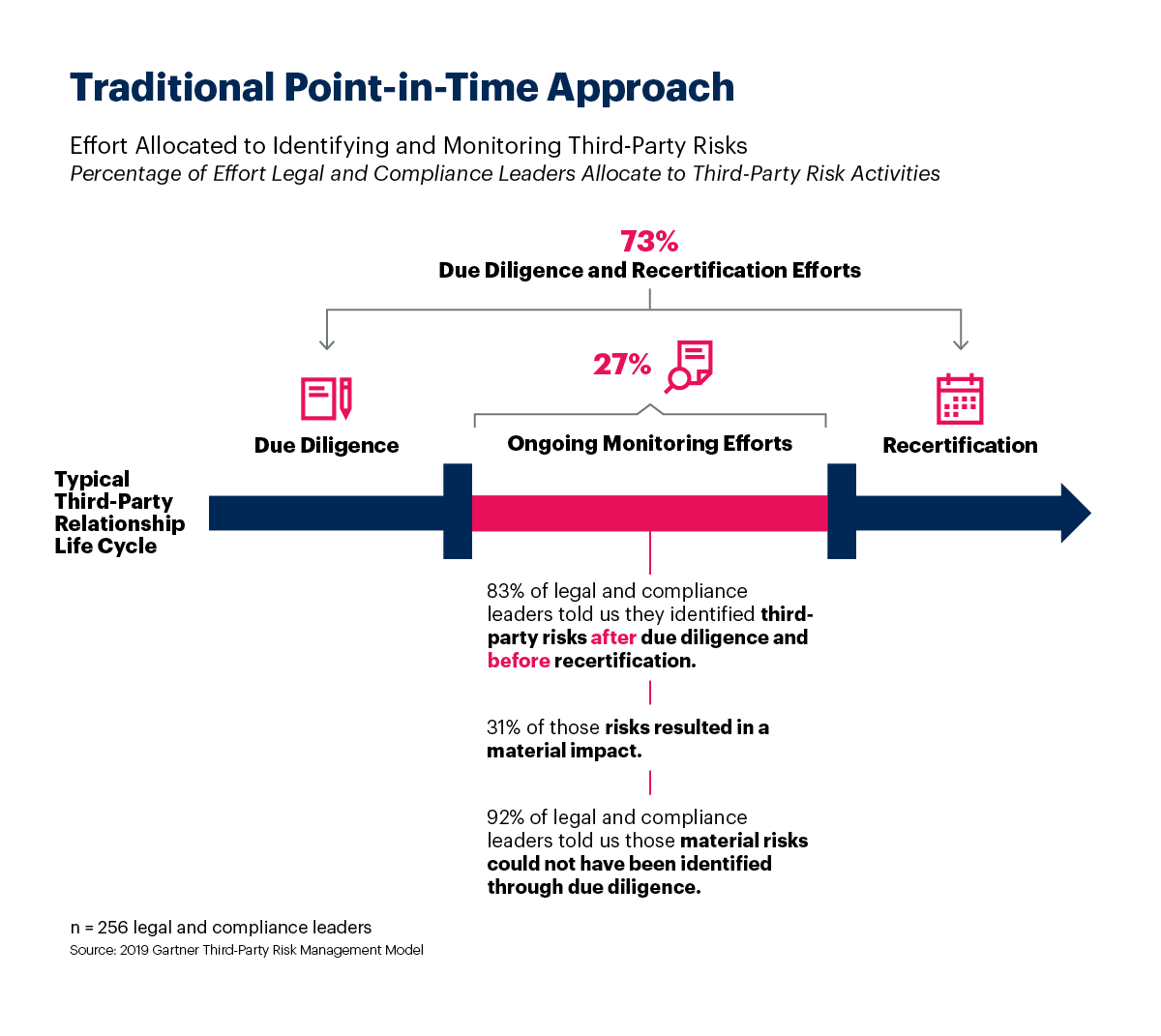
Source: Gartner
Third-Party Risk Management (TRPM) is a framework used to assess the risk level of dealing with various exterior vendors, suppliers, technology platforms, and contractors. It can be employed to evaluate all kinds of processes, but it is especially crucial when it comes to cyber security.
Retail companies often have 5 to 10 technology partners to run their stores. While this allows them tremendous efficiency gains, all these external players can quickly become weak points if not properly assessed.
The two biggest breaches in recent events, previously mentioned Target and Home Depot hacks, resulted from improper TRPM strategy.
TRPM best practices
Identifying potential TRPM risks is one thing; maintaining standards for all third-party vendors is another.
Make sure it’s more than a basic inspection, and try to collaborate directly with your partners to develop cyber security awareness programs for your staff explicitly tailored to their roles.
The main danger of third-party software and hardware vendors is that employees are often unfamiliar with them. This means they aren’t properly trained to detect when a software is infected or running erratically.
Another potentially dizzying aspect of TRPM is that each hardware your vendor uses has its own supply chain of vendors and partners.
For example, a certain type of chip or operating system could be infected, leading to a breach for everyone in the network. This is where constant communication with technology partners and third-party risk management training becomes essential for retail IT departments.
Cyber Security Awareness Training is the Answer
The common thread for most retail cyber attacks is the wide variety of technology used at nearly all stores worldwide. Since retailers have high turnover rates, they often skip cyber security training for their employees for many reasons, including saving resources.
But this can easily be the exact reason why they must be part of a robust cyber security awareness program.
Even when all parties involved do their job to stay secure, your employees will always be the first line of defense. If they are well-equipped and trained, they’ll be able to detect issues ahead of time and potentially save you and your customers from a sticky situation.
![]()
Gaining awareness of how your organization stands against a cyber attack is the first step to strengthening your defenses
See how equipped your employees are to detect and protect your business against cyber threats.