
Business Email Compromise (BEC) is a phishing email scam that typically targets employees of companies who regularly send wire transfers to their partners or third-party vendors.
Occasionally referred to as "man-in-the-email," Business Email Compromise uses spoofed or compromised email accounts to trick email recipients into providing company information, sending money, or sharing company innovations and technology.
BEC uses social engineering techniques to impersonate company executives, accounting departments of foreign partners, and other senior members of the company and win the trust of the email recipient.
Cyber criminals behind these scams know that most people don't scrutinize sender email addresses or notice slight URL discrepancies.
Along with familiar, urgent, and strategic email wording, these techniques make it difficult for company employees to recognize BEC threats.
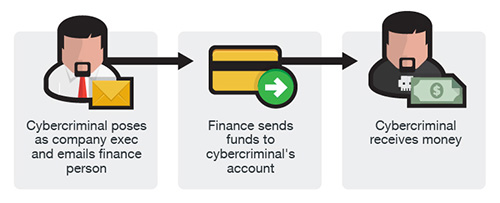
How Common is BEC?
According to the Financial Services Sharing and Analysis Center (FS-ISAC), BEC crimes saw a 300% increase in 2022 from the prior year. The Federal Bureau of Investigation tells a similar story, slotting BEC as one of the costliest cyber crimes to date.
Between April 2022 and April 2023 alone, Microsoft Threat Intelligence detected 35 million BEC attempts, with an average of 156,000 daily attempts.
The above statistics reinforce how prevalent and dangerous BEC attacks are to companies and individuals tricked into giving up money, company information, and technology.
Watch the following video about preventing BEC with security awareness and phishing simulations to understand how easy it is for anyone to become a victim of a BEC scam.
Types of Business Email Compromise
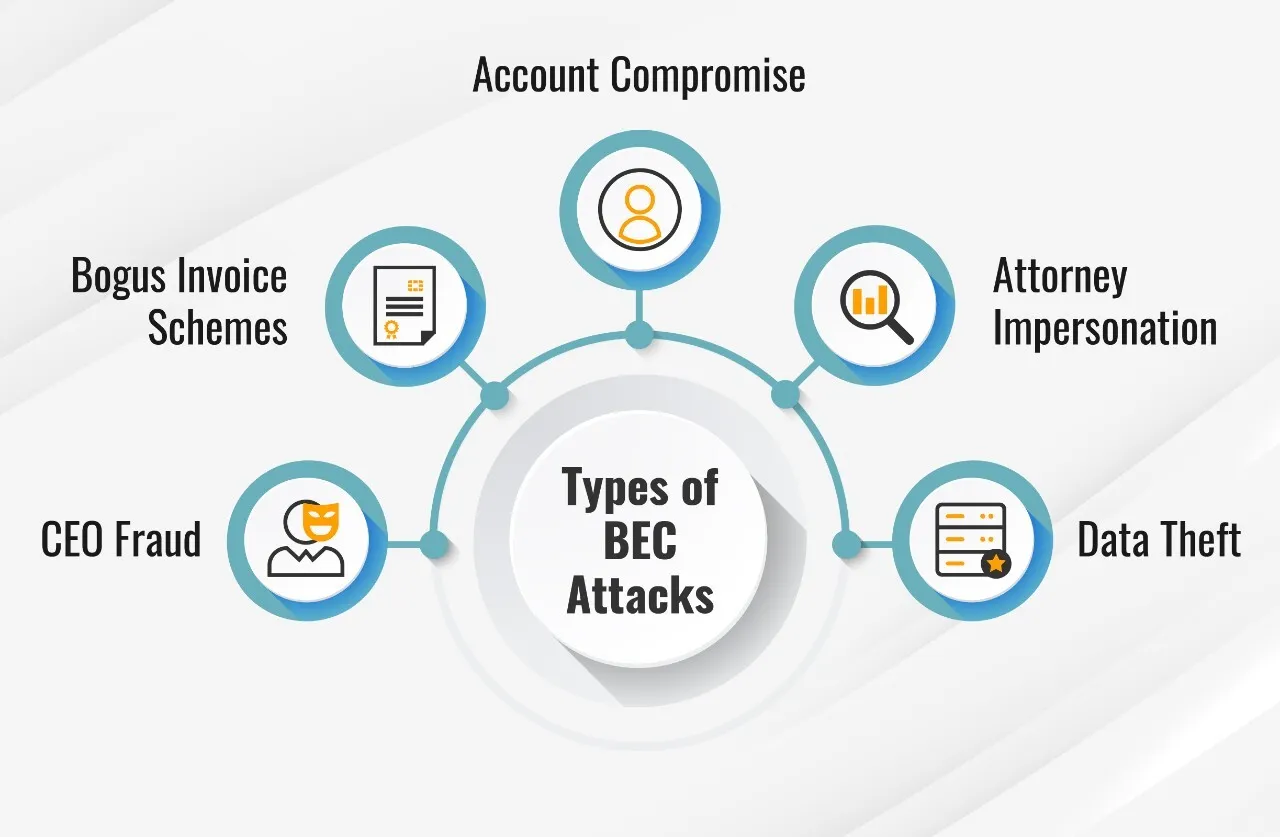

CEO Fraud
The cyber criminal spoofs a company executive's email account and then uses this identification to steal from the company. Typically, the spoofed email account will differ slightly from the actual account—for example, [email protected] instead of [email protected].
Using this email address and identity, the cyber criminal sends an email with a subject line and message requesting an urgent money transfer. The email recipient trusts the sender and does not feel compelled to double-check the email address for accuracy.
The email recipient sends the funds as asked and doesn't think to verify the bank name or company name associated with the transfer.

Bogus Invoice Scheme
Using malware or another phishing technique, the cyber criminal infiltrates the company's email system. The cyber criminal then takes over an employee email account typically used to request invoice payments and fund transfers.
Often with an urgent tone, the cyber criminal emails the compromised account asking another employee to transfer funds or make an invoice payment to a specific account.
The targeted employee trusts the email sender and inadvertently sends funds to a fraudulent account connected to the cyber criminal.
The cyber criminal emails the compromised account asking another employee to transfer funds or make an invoice payment to a specific account. Often the email is written with an urgent tone. The targeted employee trusts the email sender and inadvertently sends funds to a fraudulent account connected to the cyber criminal.

Account Compromise
Using savvy phishing techniques, cyber criminals hack an employee's account to mine the victim's contact list for company vendors, partners, and suppliers.
Emails are then sent from the hacked account to these critical contacts requesting payments be sent to a fake account controlled by the cyber criminal.

Attorney Impersonation
This type of BEC is when a cyber criminal poses as a lawyer acting on behalf of a client and contacts company employees or the CEO. The perpetrator makes it clear that this email conversation is time-sensitive and should be kept confidential.
Feeling pressured and believing they're doing the right thing, the BEC victim sends the requested funds.
Savvy cyber criminals often use this BEC scheme on a Friday afternoon or before the start of a holiday when they know the email recipient is rushing to get work done.

Data Theft
The cyber criminal takes over the company email of one or more human resources team members. These email addresses are used to request confidential information about employees, the company, partners, and investors.
The cyber criminal later uses this data as part of a more significant BEC attack or a more advanced cyber attack against the company.
How Business Email Compromise Works
Because of the nature of the crime, a BEC attack requires a strategic and thorough approach.

Typically, employees believe they're acting in the organization's best interest by paying an overdue invoice or transferring funds to a new company partner.
It's important to remember that BEC schemes rely on savvy social engineering techniques and the human element of trust.
Phishing simulations allow you to identify which employees are prone to BEC scams and phishing attacks, demonstrating how easy it is for cyber security attacks like BEC to happen.
How To Prevent BEC Attacks
To prevent BEC attacks, do the following:
What is a Phishing Simulation?
Phishing simulation is the best way to raise awareness of BEC risks and identify which employees are at risk for BEC scams and phishing.
BEC relies on phishing techniques to access the company email system and uses social engineering techniques to convince employees to act as requested.
Phishing simulation lets you easily incorporate cyber security awareness training into your organization in an interactive and informative format.
People see first-hand how personalized trustworthy emails are used to steal personal and corporate information. Real-time BEC and phishing simulations are ideal for any organization to educate people and increase alertness levels to BEC schemes and techniques.
How Can Phishing Simulations Help Prevent BEC?
Phishing simulations allow you to show employees in real time how easy it is to fall victim to a BEC attack. Using real-world examples and sophisticated phishing simulations, phishing simulations help employees realize why verifying email addresses and confirming requests for funds or confidential information is essential before acting.
Phishing simulations give your organization these top 10 benefits in the defense against BEC scams and other cyber security threats:
How to Learn More About BEC
To learn more about BEC and how you can keep your organization cyber secure, take advantage of our free cyber security awareness resources:
We are committed to delivering people-centric training that makes your organization cyber security aware.